FBI and CISA warn of attacks by Rhysida ransomware gang
Security Affairs
NOVEMBER 15, 2023
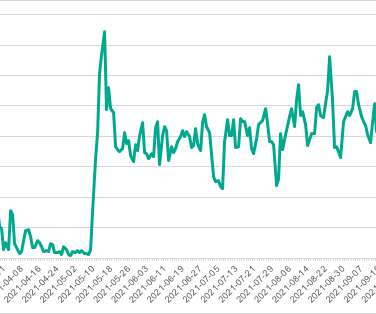
The ransomware gang hit organizations in multiple industries, including the education, healthcare, manufacturing, information technology, and government sectors. PuTTY.exe Rhysida actors have been observed creating Secure Shell (SSH) PuTTy connections for lateral movement. The victims of the group are “targets of opportunity.”














































Let's personalize your content