IoT and Quantum Computing’s Impact on the Federal Government
Thales Cloud Protection & Licensing
SEPTEMBER 17, 2019
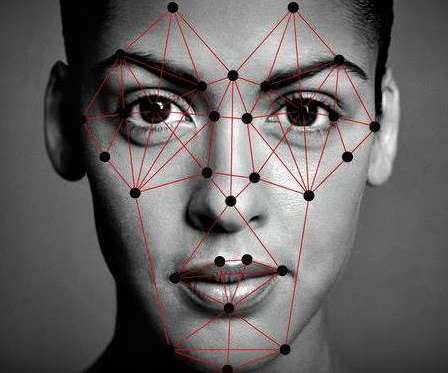
As government agencies get back to work after summer barbeques, family vacations and once-in-a-lifetime getaways, the focus is on the priorities for the rest of 2019. Cybersecurity remains one of the top concerns and priorities for our government. The Continued Impact of IoT. I can say we are closer than ever to quantum.











































Let's personalize your content