LastPass Data Breach: It's Time to Ditch This Password Manager
WIRED Threat Level
DECEMBER 28, 2022
The password manager's most recent data breach is so concerning, users need to take immediate steps to protect themselves.
WIRED Threat Level
DECEMBER 28, 2022
The password manager's most recent data breach is so concerning, users need to take immediate steps to protect themselves.

Dark Reading
DECEMBER 29, 2022
Attackers are harvesting credentials from compromised systems. Here's how some commonly used tools can enable this.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Krebs on Security
DECEMBER 19, 2022
Photo: BrandonKleinPhoto / Shutterstock.com. Two U.S. men have been charged with hacking into the Ring home security cameras of a dozen random people and then “swatting” them — falsely reporting a violent incident at the target’s address to trick local police into responding with force. Prosecutors say the duo used the compromised Ring devices to stream live video footage on social media of police raiding their targets’ homes, and to taunt authorities when they arri
Krebs on Security
DECEMBER 13, 2022
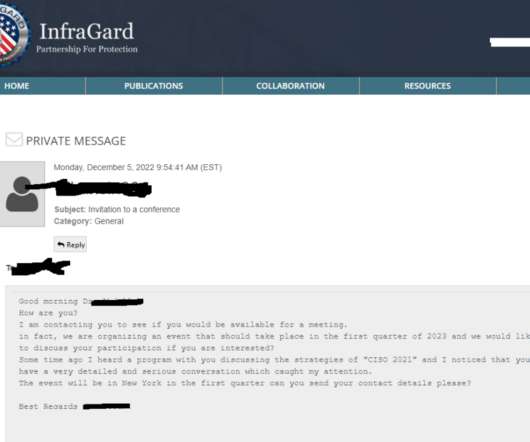
InfraGard , a program run by the U.S. Federal Bureau of Investigation (FBI) to build cyber and physical threat information sharing partnerships with the private sector, this week saw its database of contact information on more than 80,000 members go up for sale on an English-language cybercrime forum. Meanwhile, the hackers responsible are communicating directly with members through the InfraGard portal online — using a new account under the assumed identity of a financial industry CEO tha

Advertisement
With its unparalleled flexibility, rapid development and cost-saving capabilities, open source is proving time and again that it’s the leader in data management. But as the growth in open source adoption increases, so does the complexity of your data infrastructure. In this Analyst Brief developed with IDC, discover how and why the best solution to this complexity is a managed service, including: Streamlined compliance with some of the most complex regulatory guidelines Simplified operations, li

Data Breach Today
DECEMBER 19, 2022
Move Infrastructure to the Cloud and Hone Incident Response Plans, Experts Say To avoid having to even consider paying a ransom, experts have long urged all organizations to put in place appropriate defenses. Two defensive strategies for healthcare firms are moving backup and recovery to the cloud and practicing incident response scenarios.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Security Affairs
DECEMBER 2, 2022
Qualys researchers demonstrated how to chain a new Linux flaw with two other two issues to gain full root privileges on an impacted system. Researchers at the Qualys’ Threat Research Unit demonstrated how to chain a new Linux vulnerability, tracked as CVE-2022-3328 , with two other flaws to gain full root privileges on an affected system. The vulnerability resides in the snap-confine function on Linux operating systems, a SUID-root program installed by default on Ubuntu.

Schneier on Security
DECEMBER 30, 2022
Yet another smartphone side-channel attack: “ EarSpy: Spying Caller Speech and Identity through Tiny Vibrations of Smartphone Ear Speakers “: Abstract: Eavesdropping from the user’s smartphone is a well-known threat to the user’s safety and privacy. Existing studies show that loudspeaker reverberation can inject speech into motion sensor readings, leading to speech eavesdropping.

KnowBe4
DECEMBER 10, 2022
ChatGPT could give Google a serious run for its money. We are not quite there yet, but the capabilities are rapidly improving. Just have a look at the command I gave it. In 5 seconds the copy rolled out.

Krebs on Security
DECEMBER 14, 2022
The U.S. Department of Justice (DOJ) today seized four-dozen domains that sold “booter” or “stresser” services — businesses that make it easy and cheap for even non-technical users to launch powerful Distributed Denial of Service (DDoS) attacks designed knock targets offline. The DOJ also charged six U.S. men with computer crimes related to their alleged ownership of the popular DDoS-for-hire services.

Advertisement
The complexity of financial data, the need for real-time insight, and the demand for user-friendly visualizations can seem daunting when it comes to analytics - but there is an easier way. With Logi Symphony, we aim to turn these challenges into opportunities. Our platform empowers you to seamlessly integrate advanced data analytics, generative AI, data visualization, and pixel-perfect reporting into your applications, transforming raw data into actionable insights.

Data Breach Today
DECEMBER 13, 2022
Victims Still Learning Their Personal Data Was Illegally Accessed, Copied in 2021 A ransomware attack on the Irish healthcare system in 2021 has cost the government 80 million euros in damages and counting. The Irish Health Service continues to notify victims of the incident that their personal information was illegally accessed and copied.

eSecurity Planet
DECEMBER 7, 2022
It has certainly been a rough year for the tech industry. There have been many layoffs, the IPO market has gone mostly dark, and venture funding has decelerated. Despite all this, there is one tech category that has held up fairly well: Cybersecurity. Just look at a report from M&A advisory firm Houlihan Lokey , which found that private cybersecurity company funding grew by 9.4% to $26.9 billion between September 2021 and September 2022.
Security Affairs
DECEMBER 1, 2022
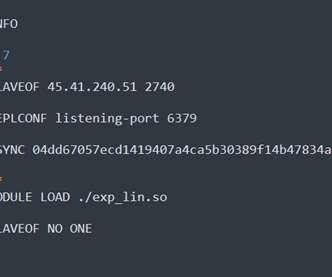
Redigo is a new Go-based malware employed in attacks against Redis servers affected by the CVE-2022-0543 vulnerability. Researchers from security firm AquaSec discovered a new Go-based malware that is used in a campaign targeting Redis servers. Threat actors are exploiting a critical vulnerability, tracked as CVE-2022-0543 , in Redis (Remote Dictionary Server) servers.

IT Governance
DECEMBER 20, 2022
2022 will go down as the year where some semblance of normality returned. Social distancing restrictions were gone, masks disappeared and we made travel plans unfettered by fear of positive lateral flow tests. These were truly precedented times. Although there have still been a few surprises, with the death of Queen Elizabeth II and blazing heatwaves across the UK to name but two, it was a familiar year in the cyber security landscape.

Advertisement
Adding high-quality entity resolution capabilities to enterprise applications, services, data fabrics or data pipelines can be daunting and expensive. Organizations often invest millions of dollars and years of effort to achieve subpar results. This guide will walk you through the requirements and challenges of implementing entity resolution. By the end, you'll understand what to look for, the most common mistakes and pitfalls to avoid, and your options.

Dark Reading
DECEMBER 6, 2022
Threat actors can weaponize code within AI technology to gain initial network access, move laterally, deploy malware, steal data, or even poison an organization's supply chain.

Krebs on Security
DECEMBER 8, 2022
Ransomware groups are constantly devising new methods for infecting victims and convincing them to pay up, but a couple of strategies tested recently seem especially devious. The first centers on targeting healthcare organizations that offer consultations over the Internet and sending them booby-trapped medical records for the “patient.” The other involves carefully editing email inboxes of public company executives to make it appear that some were involved in insider trading.

Data Breach Today
DECEMBER 20, 2022
Breach Is Latest in Long List of Complex Vendor Incidents An Oklahoma-based provider of administrative and technology services to healthcare organizations is notifying more than 271,000 individuals that their personal information may have been compromised in a hacking incident involving a third-party data storage vendor.
eSecurity Planet
DECEMBER 8, 2022
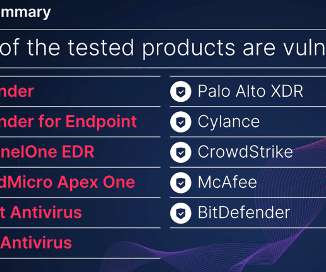
SafeBreach Labs researcher Or Yair has uncovered zero-day vulnerabilities in several leading endpoint detection and response ( EDR ) and antivirus ( AV ) solutions that enabled him to turn the tools into potentially devastating next-generation wipers. “This wiper runs with the permissions of an unprivileged user yet has the ability to wipe almost any file on a system, including system files, and make a computer completely unbootable,” Yair warned in a blog post detailing the findings

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, VP of Engineering at Betterworks, will explore a practical framework to transform Generative AI pr

Security Affairs
DECEMBER 19, 2022
IT giant Cisco is warning of threat actors exploiting many old vulnerabilities in attacks in the wild. Cisco has updated multiple security advisories to warn of the active exploitation of several old vulnerabilities impacting its products. The bugs, some of which are rated as ‘critical’ severity, impact Cisco IOS, NX-OS, and HyperFlex software. Below are the critical vulnerabilities being exploited in attacks in the wild: CVE-2017-12240 (CVSS score of 9.8) – The vulnerability affects the D

Thales Cloud Protection & Licensing
DECEMBER 21, 2022
Thales collaborates with Hewlett Packard Enterprise to Enhance 5G Subscriber Privacy and Security. divya. Thu, 12/22/2022 - 05:40. Thales collaborates with Hewlett Packard Enterprise (HPE) to provide enhanced privacy and secure authentication for global 5G users, further extending its partner ecosystem. The Thales Luna 7 Hardware Security Module (HSM), a world-class HSM, will power a foundation of trust around HPE’s Subscriber Data Management (SDM) solutions, ensuring subscriber data, transactio

Schneier on Security
DECEMBER 5, 2022
This is an actual CAPTCHA I was shown when trying to log into PayPal. As an actual human and not a bot, I had no idea how to answer. Is this a joke? (Seems not.) Is it a Magritte-like existential question? (It’s not a bicycle. It’s a drawing of a bicycle. Actually, it’s a photograph of a drawing of a bicycle. No, it’s really a computer image of a photograph of a drawing of a bicycle.

Krebs on Security
DECEMBER 20, 2022
Millions of people likely just received an email or snail mail notice saying they’re eligible to claim a class action payment in connection with the 2017 megabreach at consumer credit bureau Equifax. Given the high volume of reader inquiries about this, it seemed worth pointing out that while this particular offer is legit (if paltry), scammers are likely to soon capitalize on public attention to the settlement money.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Data Breach Today
DECEMBER 2, 2022
Some Customers at Risk of Identity Theft, South Staffordshire Water Belatedly Warns Is a four-month delay between learning your systems were breached and notifying affected customers acceptable? After spotting an attack in August, private utility South Staffordshire Water in England is only beginning to alert customers that they're at risk of identity theft.

eSecurity Planet
DECEMBER 1, 2022
The Wiz Research Team recently discovered a supply chain vulnerability in IBM Cloud that they say is the first to impact a cloud provider’s infrastructure. In a dramatic flair, they named the flaw Hell’s Keychain. The security issues were reported to IBM Cloud in late August, and were patched in early September. Before it was patched, an attacker with knowledge of the vulnerability could run malicious code and modify data being stored by any IBM Cloud customer using PostgreSQL.
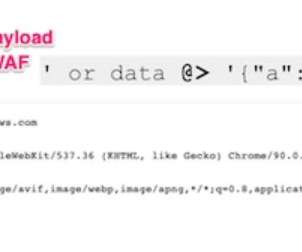
Security Affairs
DECEMBER 9, 2022
Claroty researchers devised a technique for bypassing the web application firewalls (WAF) of several vendors. Researchers at industrial and IoT cybersecurity firm Claroty devised an attack technique for bypassing the web application firewalls (WAF) of several industry-leading vendors. The technique was discovered while conducting unrelated research on Cambium Networks’ wireless device management platform.

Dark Reading
DECEMBER 8, 2022
Common mistakes in network configuration can jeopardize the security of highly protected assets and allow attackers to steal critical data from the enterprise.

Speaker: Nicholas Zeisler, CX Strategist & Fractional CXO
The first step in a successful Customer Experience endeavor (or for that matter, any business proposition) is to find out what’s wrong. If you can’t identify it, you can’t fix it! 💡 That’s where the Voice of the Customer (VoC) comes in. Today, far too many brands do VoC simply because that’s what they think they’re supposed to do; that’s what all their competitors do.

Schneier on Security
DECEMBER 8, 2022
A bunch of Android OEM signing keys have been leaked or stolen, and they are actively being used to sign malware. Łukasz Siewierski, a member of Google’s Android Security Team, has a post on the Android Partner Vulnerability Initiative (AVPI) issue tracker detailing leaked platform certificate keys that are actively being used to sign malware.
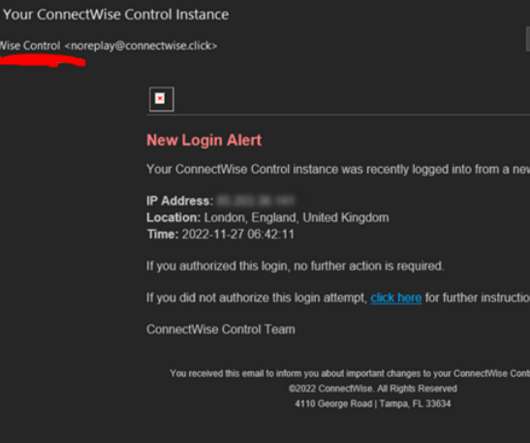
Krebs on Security
DECEMBER 1, 2022
ConnectWise , which offers a self-hosted, remote desktop software application that is widely used by Managed Service Providers (MSPs), is warning about an unusually sophisticated phishing attack that can let attackers take remote control over user systems when recipients click the included link. The warning comes just weeks after the company quietly patched a vulnerability that makes it easier for phishers to launch these attacks.

Data Breach Today
DECEMBER 8, 2022
Indian Firm Accuses 'Notorious Cyber Security Company' in Ongoing Incident Indian cybersecurity firm CloudSEK says another cybersecurity firm used a compromised collaboration platform credential to obtain access to its training webpages. CEO Rahul Sasi did not identify the alleged perpetrator and says the hacker did not obtain access to the company code base and database.
Let's personalize your content