Weathering the Privacy Storm from GDPR to CCPA & PDPA
Dark Reading
JANUARY 23, 2020
A general approach to privacy, no matter the regulation, is the only way companies can avoid a data protection disaster in 2020 and beyond.

Dark Reading
JANUARY 23, 2020
A general approach to privacy, no matter the regulation, is the only way companies can avoid a data protection disaster in 2020 and beyond.
AIIM
JANUARY 23, 2020
This is the first part of a 3-part series on the Ethical Use of Data for Training Machine Learning Technology by guest authors Andrew Pery and Michael Simon. Part 1: Bad Things Can Come from Non-neutral Technology. AI technology is becoming pervasive , impacting virtually every facet of our lives. A recent Deloitte report estimates that shipments of devices with embedded AI will increase from 79 million in 2018 to 1.2 billion by 2022: "Increasingly, machines will learn from experiences, adapt to
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Information Management Resources
JANUARY 23, 2020
An effective program to enable business to use data while also managing risk and ensuring compliance must reflect three interlocking components: privacy, data governance and risk management.

Data Breach Today
JANUARY 23, 2020
Fraudsters Targeting Personal Information, Including Payment Card Details The FBI's Internet Crime Complaint Center has issued an alert warning that fraudsters are using spoofed job application portals and websites to steal personal information, including payment card details, from would-be applicants.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.
Security Affairs
JANUARY 23, 2020
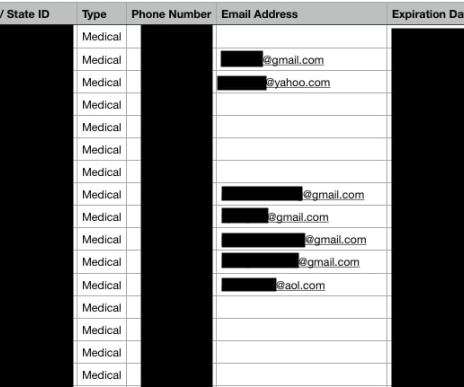
Experts found online an unsecured database owned by THSuite and used by point-of-sale systems in medical and recreational marijuana dispensaries. Data leak continues to be a frequent issue suffered by companies, news of the day is the discovery of an unsecured database owned by THSuite and used by point-of-sale systems in medical and recreational marijuana dispensaries across the United States.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

OpenText Information Management
JANUARY 23, 2020
With the patient taking center stage, digitization is gaining pace within Life Sciences. This blog looks at how digital technology is going to shape every stage of the drug lifecycle for life science and pharma companies in 2020. The post Top 5 Life Sciences predictions in 2020 appeared first on OpenText Blogs.

Data Breach Today
JANUARY 23, 2020
Agency Wants to Gather More Data to Support Security of Financial Infrastructure The U.S. Treasury Department is proposing to collect more information from banks and financial markets about the cybersecurity risks they face to help ensure the security of financial infrastructure.

Security Affairs
JANUARY 23, 2020
Hackers used a remote access Trojan (RAT) associated with Iran-linked APT groups in recent attacks on a key organization in the European energy sector. Security experts from Recorded Future reported that a backdoor previously used in attacks carried out by an Iran-linked threat actor was used to target a key organization in the European energy sector.

Data Breach Today
JANUARY 23, 2020
Researchers Discovered Unsecured Database Accessible Via Internet A point-of-sale system vendor that serves U.S. medical and recreational cannabis dispensaries left an unprotected database containing sensitive information about three clients and 30,000 of their customers exposed to the internet, researchers say.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Schneier on Security
JANUARY 23, 2020
This is new from Reuters: More than two years ago, Apple told the FBI that it planned to offer users end-to-end encryption when storing their phone data on iCloud, according to one current and three former FBI officials and one current and one former Apple employee. Under that plan, primarily designed to thwart hackers, Apple would no longer have a key to unlock the encrypted data, meaning it would not be able to turn material over to authorities in a readable form even under court order.

Data Breach Today
JANUARY 23, 2020
Five Customer Service Databases Were Left Internet-Accessible for Three Weeks Microsoft accidentally internet-exposed 250 million customer support records stored in five misconfigured Elasticsearch databases, for three weeks. While the company rapidly locked them down after being alerted, it's an embarrassing gaff for the technology giant, which has pledged to do better.

OpenText Information Management
JANUARY 23, 2020
Uncertainty has become the new norm in the energy industry and 2020 promises more of the same. This is due largely to the fact that the oil and gas and utility sectors are heavily impacted by some pretty intense forces – the geopolitical climate, trade tensions and economic fluctuations, just to name a few. Amidst … The post Top technology predictions for the energy industry in 2020 appeared first on OpenText Blogs.

Data Matters
JANUARY 23, 2020
The UK will leave the EU on January 31, 2020 ( Brexit ), under the terms of the EU (Withdrawal Agreement) Bill, which is currently going through the legislative stages of the UK Houses of Parliament, and is widely expected to enter into law. The Withdrawal Agreement includes a transition period until December 31, 2020 during which time EU law will continue to apply in the UK ( Transition Period ).

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

IT Governance
JANUARY 23, 2020
Microsoft has confirmed a massive data breach affecting anonymised data held on its customer support database. Up to 250 million records were exposed online between 5 and 31 December as a result of the tech giant failing to implement proper protections. The information, which includes email addresses, IP addresses and support case details, was held on leaky Elasticsearch servers.

IBM Big Data Hub
JANUARY 23, 2020
Teasing new O'Reilly thought leadership report being published this week. Will need help on 3 images used to drive to blog.

Dark Reading
JANUARY 23, 2020
Emotet is considered one of the most damaging banking Trojans, primarily through its ability to carry other malware into an organization.

Data Protection Report
JANUARY 23, 2020
An interim proprietary injunction has been granted by the English High Court over a bitcoin ransom payment paid to a third-party wallet. The facts. The case was brought by an English insurer (requesting anonymity) against four defendants, consisting of unknown cyber-extortionists (as well as three other parties who respectively hold and/or trade Bitcoins).

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Reltio
JANUARY 23, 2020
Customer experience. It’s one of the buzziest terms in business. And it should be. If you haven’t come to the conclusion that CX matters, volumes of research quantifies the value of providing an exceptional - or even decent - customer experience, and the perils of getting it wrong. . PwC conducted eye-popping research into the future of customer experience.

IT Governance
JANUARY 23, 2020
As part of their ISO 27001 compliance, organisations must conduct management reviews to address any emerging information security trends and to ensure that their ISMS (information security management system) works as intended. Unfortunately, there’s a mistaken belief that the review is only necessary as part of the certification audit. That couldn’t be further from the truth, as we explain in this blog.

Dark Reading
JANUARY 23, 2020
Attackers 'weaponized' Active Directory to spread the ransomware.

Security Affairs
JANUARY 23, 2020
An expert discovered that over 250 million Microsoft customer support records might have been exposed along with some personally identifiable information. The popular researcher Bob Diachenko found an unprotected database containing over 250 million customer support records along with some personally identifiable information. The unprotected archive was containing support requests submitted to the tech giant from 2005 to December 2019.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Threatpost
JANUARY 23, 2020
The malicious email campaign included a never-before-seen malware downloader called Carrotball, and may be linked to the Konni Group APT.

Dark Reading
JANUARY 23, 2020
A new document separates cloud vulnerabilities into four classes and offers mitigations to help businesses protect cloud resources.

Threatpost
JANUARY 23, 2020
New research outlines vulnerabilities in Safari’s Intelligent Tracking Protection that can reveal user browsing behavior to third parties.

DLA Piper Privacy Matters
JANUARY 23, 2020
A white paper has been leaked which provides an interesting insight into the European Union’s plans for the future regulation of artificial intelligence (“ AI ”). It follows on the heels of a spate of activity from regulators, governments and international bodies who are trying to formulate a governance strategy to respond to the exponential growth in AI development and use.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.
Dark Reading
JANUARY 23, 2020
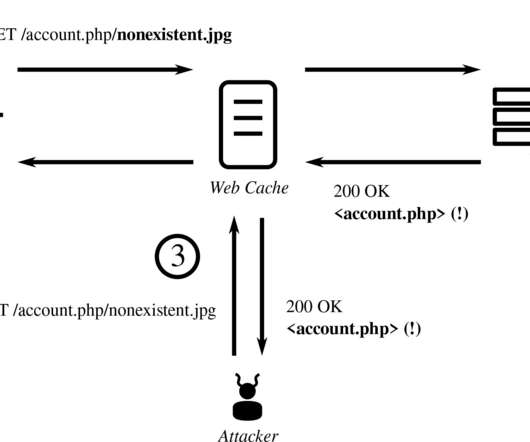
Expect cache attacks to get worse before they get better. The problem is that we don't yet have a good solution.

WIRED Threat Level
JANUARY 23, 2020
At Pwn2Own, hackers had no trouble dismantling systems that help run everything from car washes to nuclear plants—with the prize of taking home the very computers they "pwn.".

Dark Reading
JANUARY 23, 2020
CISA has released an advisory for six high-severity CVEs for GE Carescape patient monitors, Apex Pro, and Clinical Information Center systems.
Let's personalize your content