Accelerate hybrid cloud transformation through IBM Cloud for Financial Service Validation Program
IBM Big Data Hub
APRIL 4, 2024
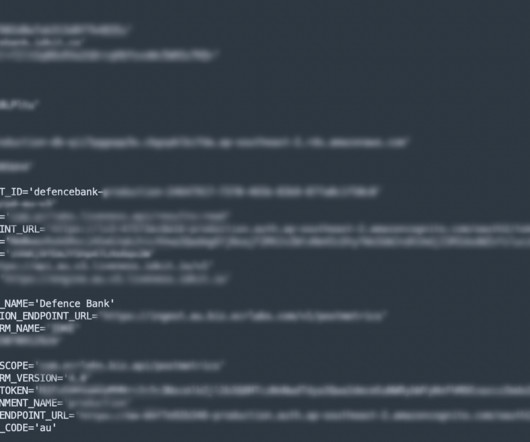
The cloud represents a strategic tool to enable digital transformation for financial institutions As the banking and other regulated industry continues to shift toward a digital-first approach, financial entities are eager to use the benefits of digital disruption. Most of these new technologies are born-in-cloud.









































Let's personalize your content