Weekly Update 294
Troy Hunt
MAY 6, 2022
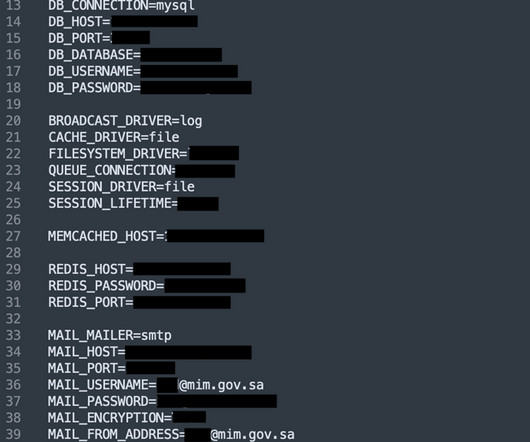
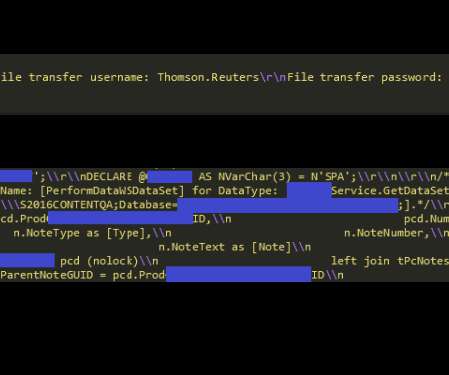
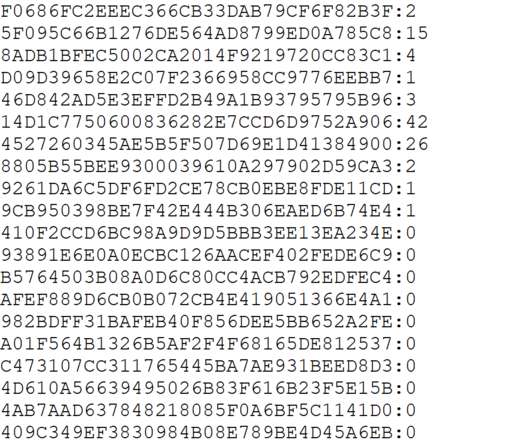
It's back to business as usual with more data breaches, more poor handling of them and more IoT pain. I think on all those fronts there's a part of me that just likes the challenge and the opportunity to fix a broken thing. Get Kolide: Device security that fixes challenging problems by messaging users on Slack.











































Let's personalize your content