‘The Manipulaters’ Improve Phishing, Still Fail at Opsec
Krebs on Security
APRIL 3, 2024
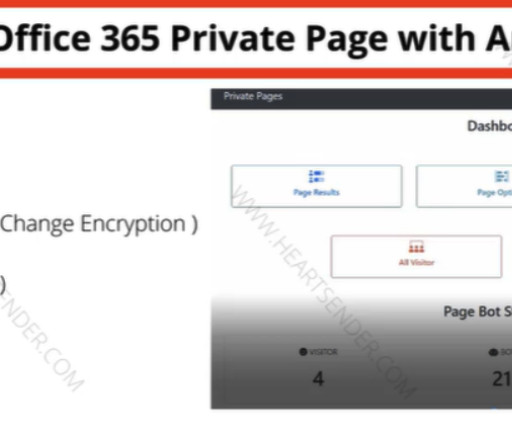
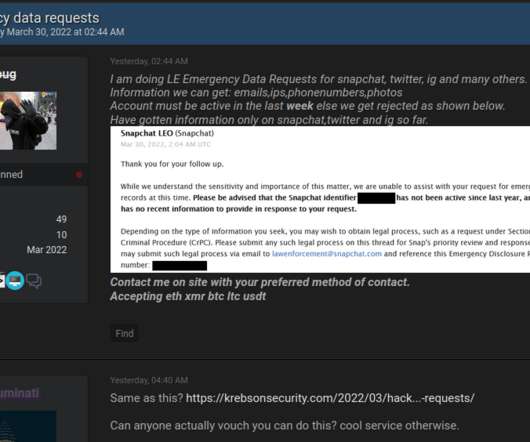
In January 2024, The Manipulaters pleaded with this author to unpublish previous stories about their work, claiming the group had turned over a new leaf and gone legitimate. Since that story ran, KrebsOnSecurity has heard from this Saim Raza identity on two occasions. The first was in the weeks following the Sept. Image: DomainTools.





































Let's personalize your content