Experts warn of an emerging Python-based credential harvester named Legion
Security Affairs
APRIL 17, 2023
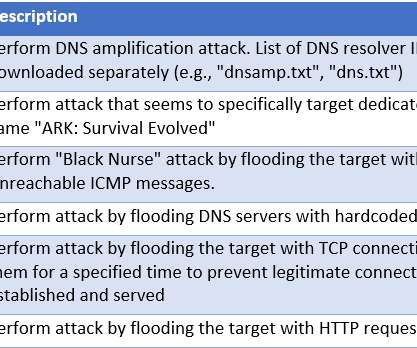
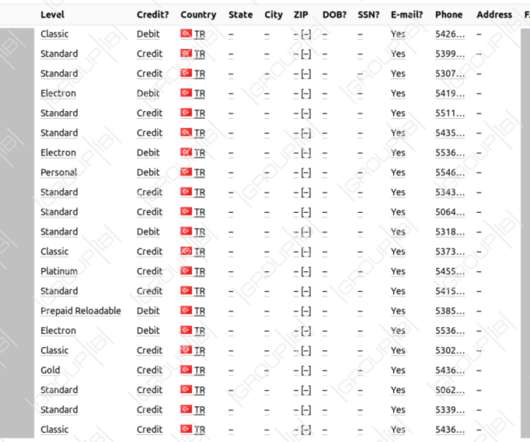
Legion is an emerging Python-based credential harvester and hacking tool that allows operators to break into various online services. Cado Labs researchers recently discovered a new Python-based credential harvester and hacking tool, named Legion, which was sold via Telegram. ” reads the analysis published by Cado Labs.

































Let's personalize your content