City of Dallas shut down IT services after ransomware attack
Security Affairs
MAY 4, 2023
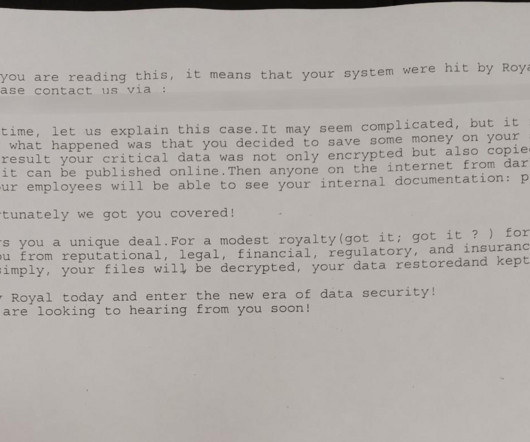
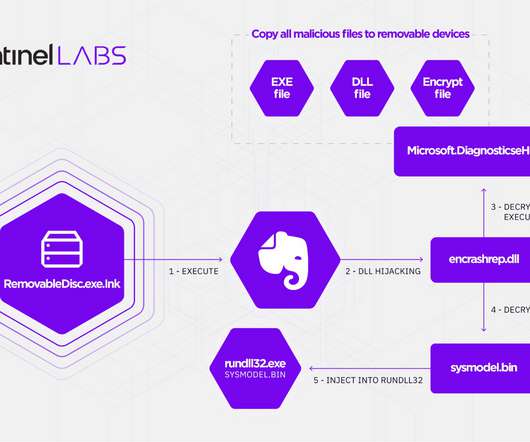
According to government experts, the Royal ransomware attacks targeted numerous critical infrastructure sectors including, manufacturing, communications, healthcare and public healthcare (HPH), and education. reads the alert.















































Let's personalize your content