Is the SEC Coming for Your Texts? SEC’s New Enforcement Director Telegraphs a Warning to Registrants About Improper Use of Personal Devices for Business-Related Communications
Data Matters
OCTOBER 13, 2021
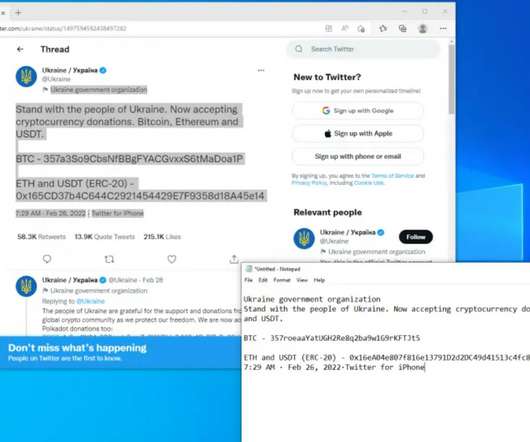
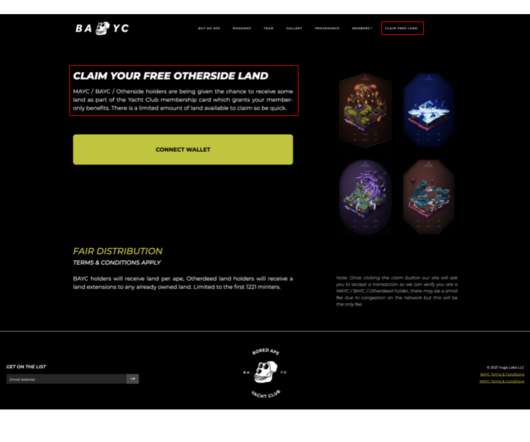
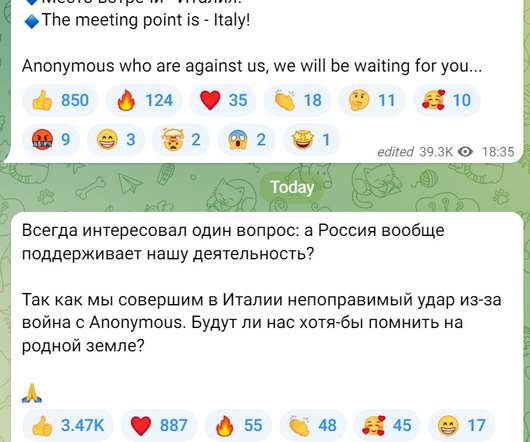
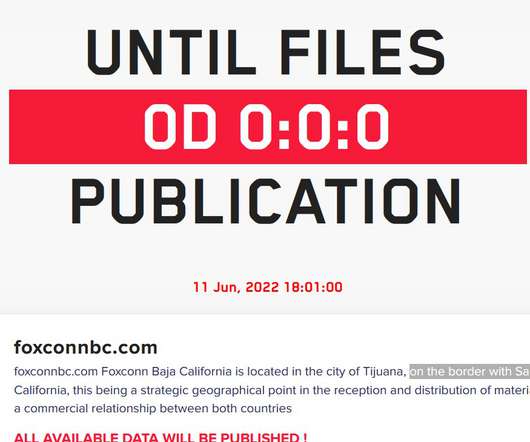
Securities and Exchange Commission (SEC) Division of Enforcement is stepping up investigative efforts looking at registered firms’ use of personal devices for business communications, which can implicate their recordkeeping obligations and result in failure to retain and produce responsive business-related communications in SEC investigations.









































Let's personalize your content