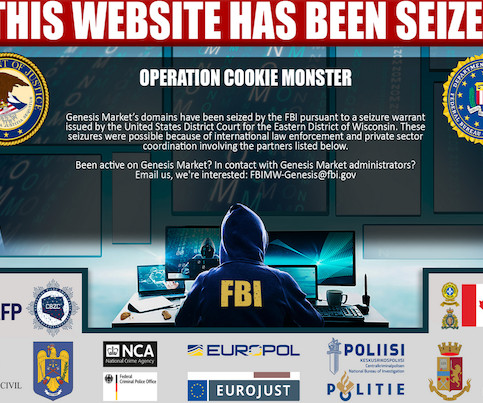
Breach Roundup: Microsoft Deprecates NTLM Authentication
Data Breach Today
JUNE 6, 2024
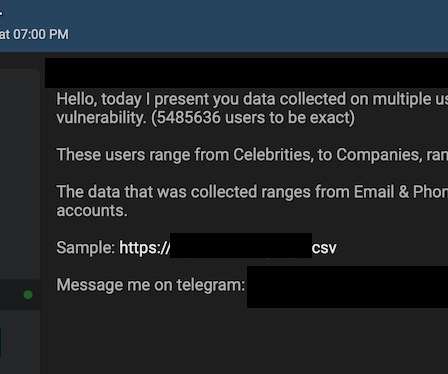
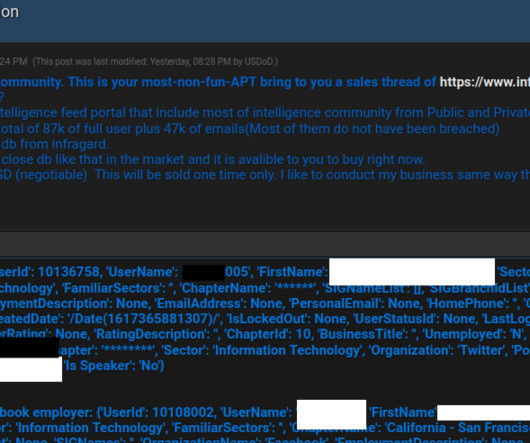
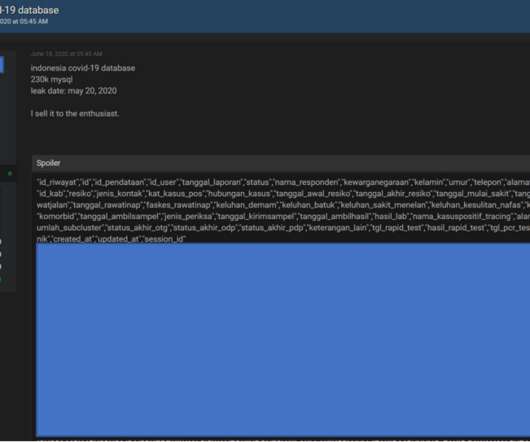
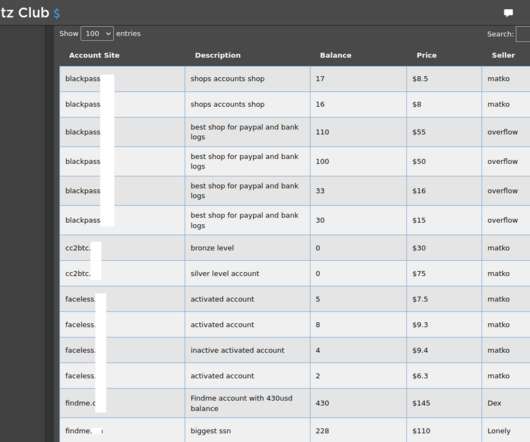
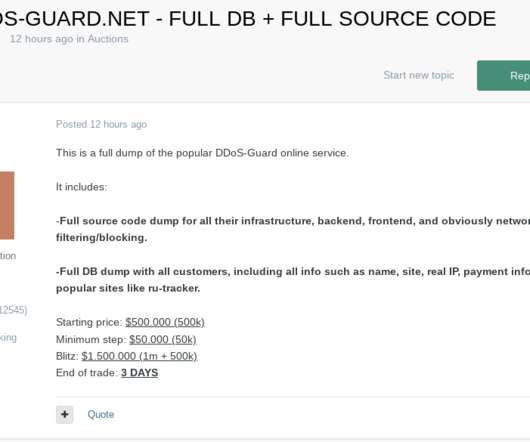
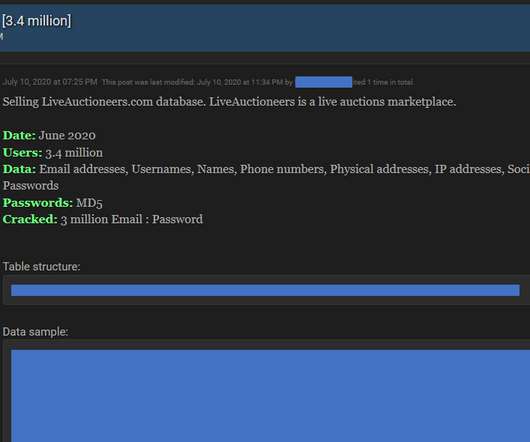
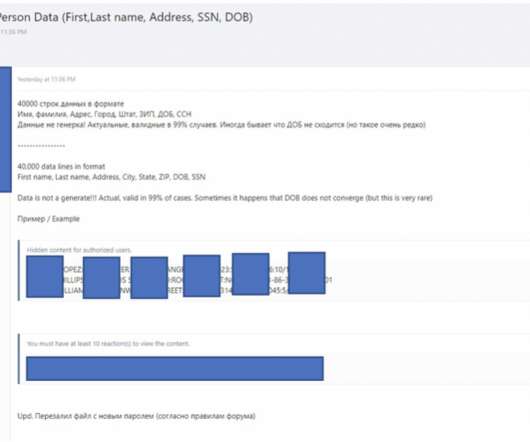
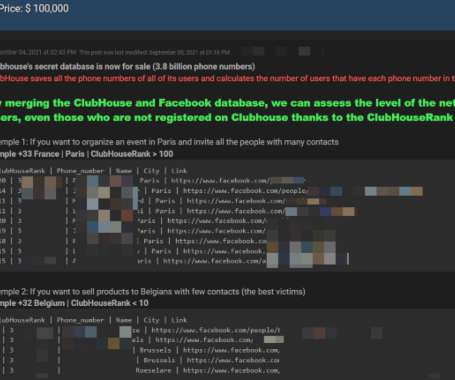
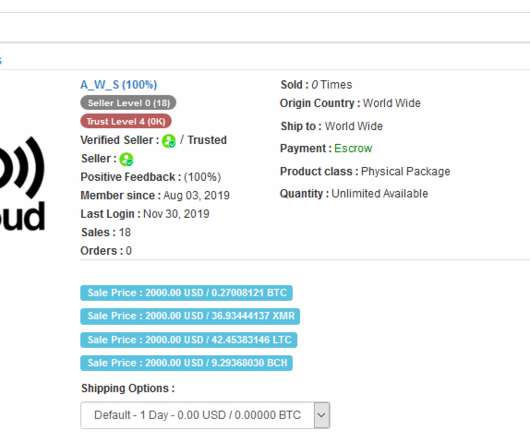
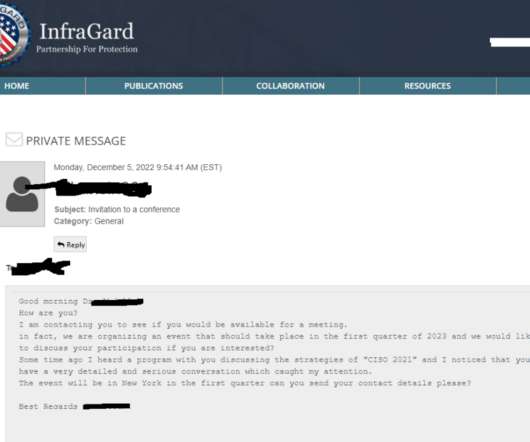
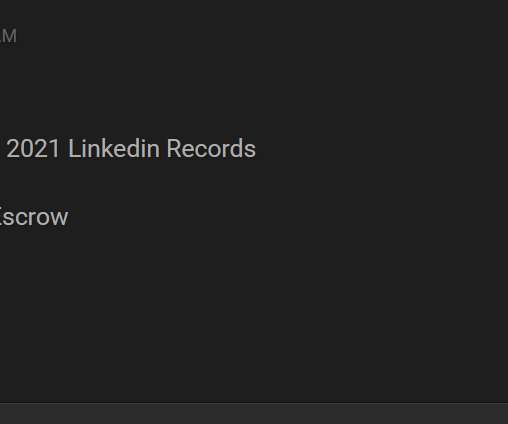
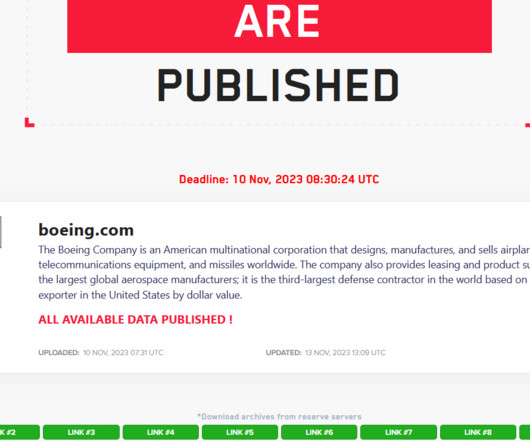
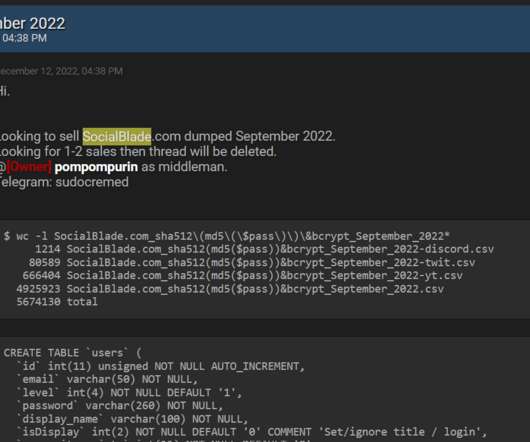
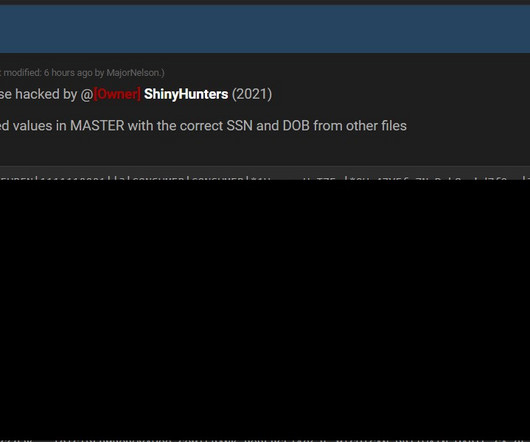
Also: Hacker Sells Data Obtained Through Snowflake Attack This week, Microsoft deprecated NTLM authentication, a hacker put apparently stolen Snowflake data up for sale, Ticketmaster confirmed its breach, Cisco patched Webex vulnerabilities, pro-Russian hacktivists claimed a DDoS attack in Spain and Kaspersky launched a free virus removal tool for (..)






























Let's personalize your content