Threat actors actively exploit JetBrains TeamCity flaws to deliver malware
Security Affairs
MARCH 20, 2024
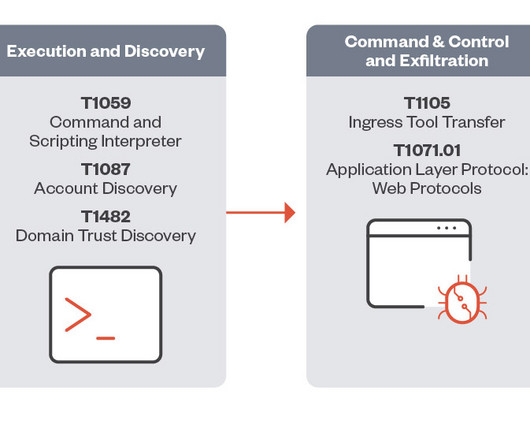
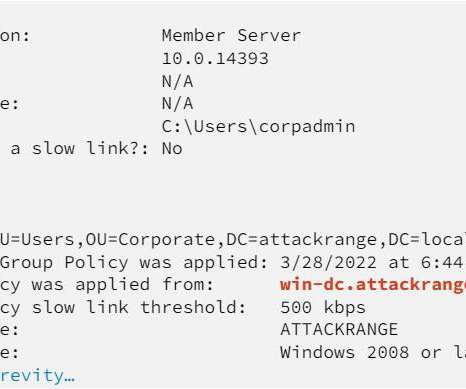
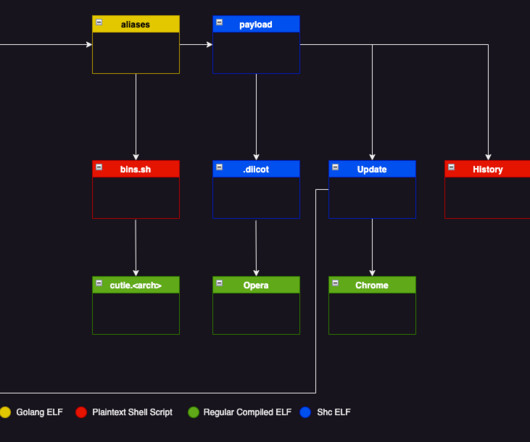
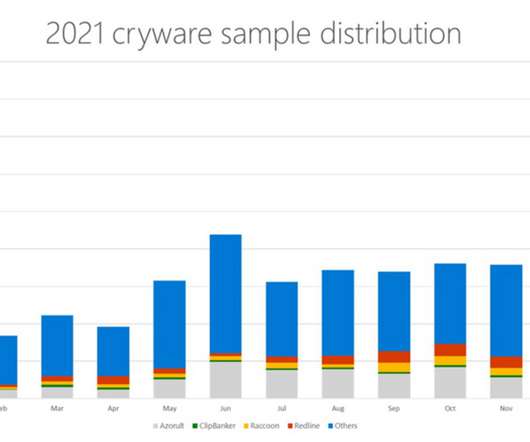
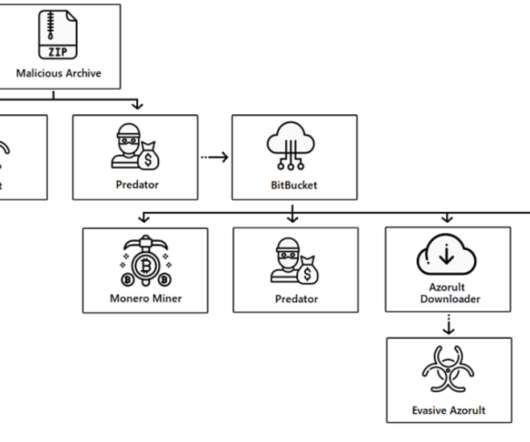
security flaws in JetBrains TeamCity to deploy multiple malware families and gain administrative control over impacted systems. In early March, Rapid7 researchers disclosed two new critical security vulnerabilities, tracked as CVE-2024-27198 (CVSS score: 9.8) and CVE-2024-27199 (CVSS score:7.3), in JetBrains TeamCity On-Premises.
































Let's personalize your content