Threat actors actively exploit JetBrains TeamCity flaws to deliver malware
Security Affairs
MARCH 20, 2024
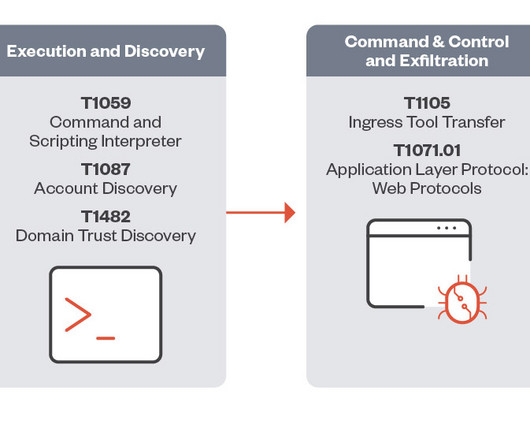
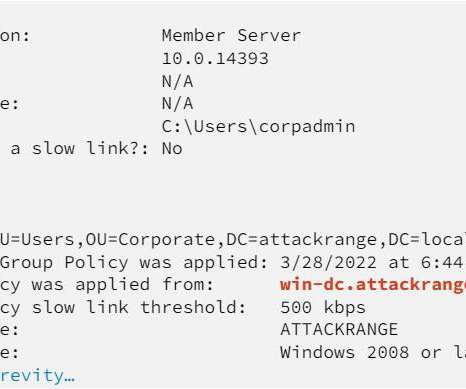
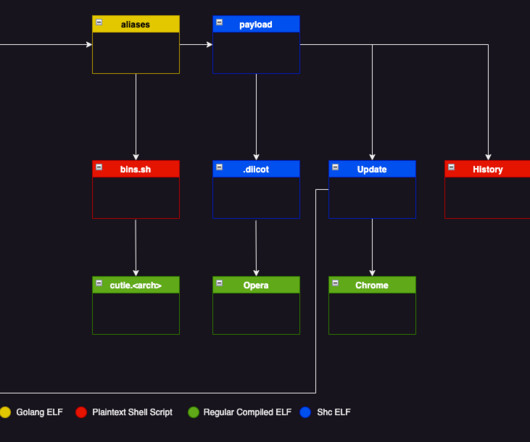
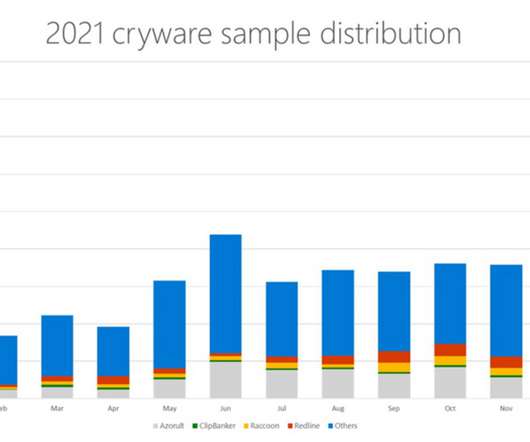
Below are the descriptions for these vulnerabilities: CVE-2024-27198 is an authentication bypass vulnerability in the web component of TeamCity that arises from an alternative path issue ( CWE-288 ) and has a CVSS base score of 9.8 reads the advisory published by JetBrains. it was addressed with the release of version 2023.11.4.
































Let's personalize your content