UAC-0020 threat actor used the SPECTR Malware to target Ukraine’s defense forces
Security Affairs
JUNE 7, 2024
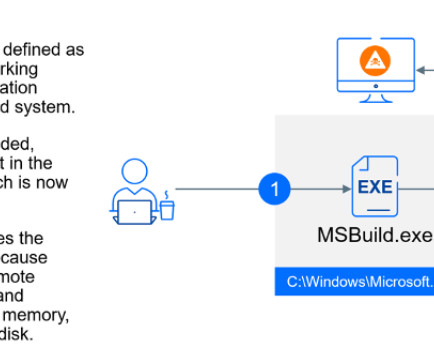
The UA-CERT states that the “sync.exe” file contains the legitimate SyncThing components and SPECTR malware files, including additional libraries and scripts.























Let's personalize your content