AI in retail and the rise of the purpose-driven consumer
IBM Big Data Hub
FEBRUARY 21, 2022
That retail has experienced extreme disruption in recent years is beyond questioning. Even before Covid turned the world on its head, headlines about the so-called “retail apocalypse” were near-ubiquitous in the media. Retail isn’t just big, it’s huge — the National Retail Federation expects sales to grow by as much as 13.5%





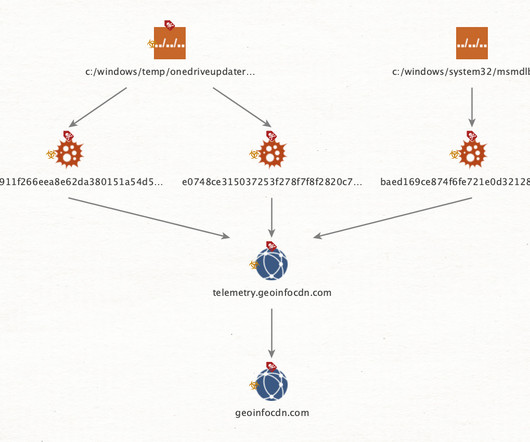

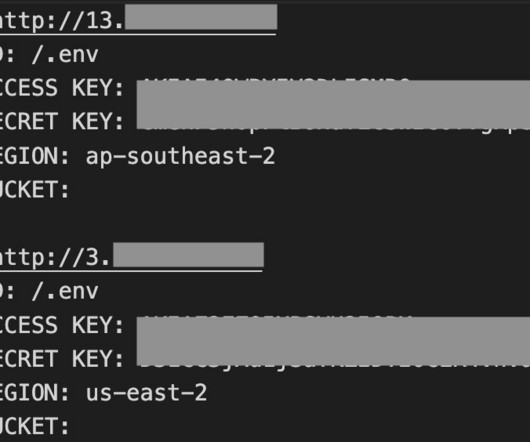





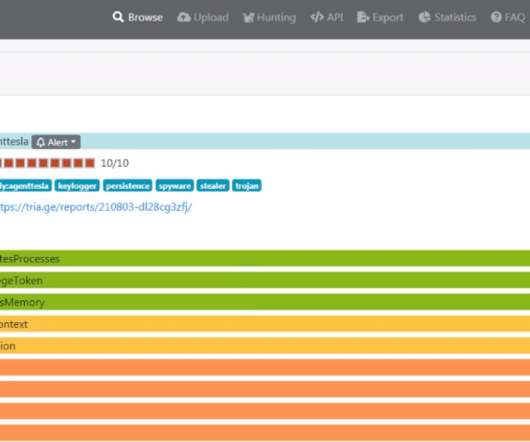










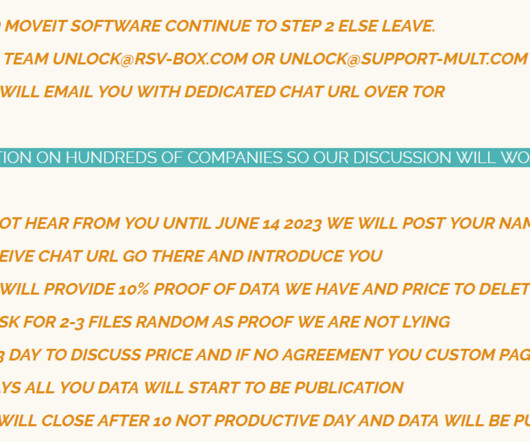























Let's personalize your content