Leveraging user-generated social media content with text-mining examples
IBM Big Data Hub
AUGUST 28, 2023
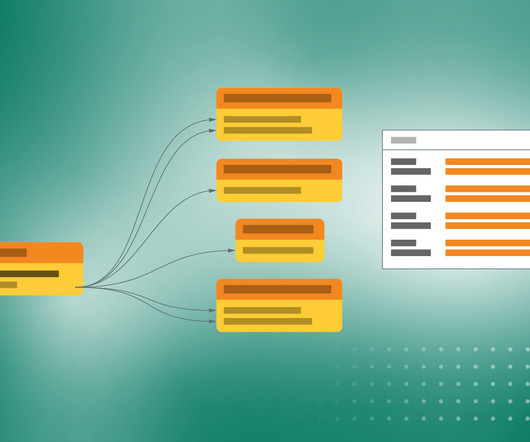
One of the best ways to take advantage of social media data is to implement text-mining programs that streamline the process. What is text mining? Text analysis takes it a step farther by focusing on pattern identification across large datasets, producing more quantitative results. How does text mining work?



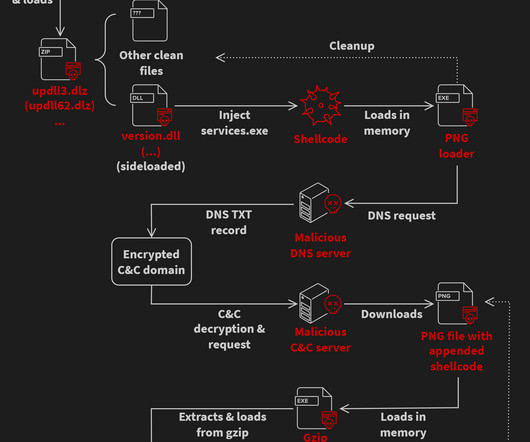
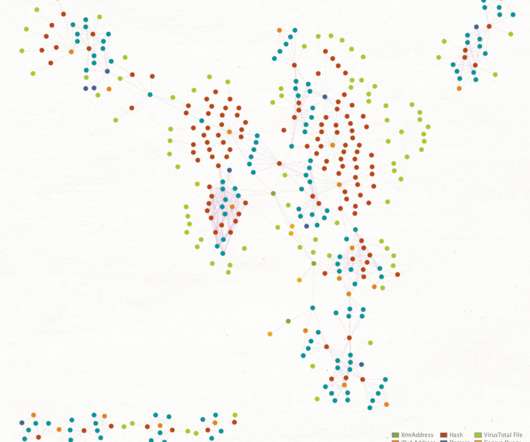




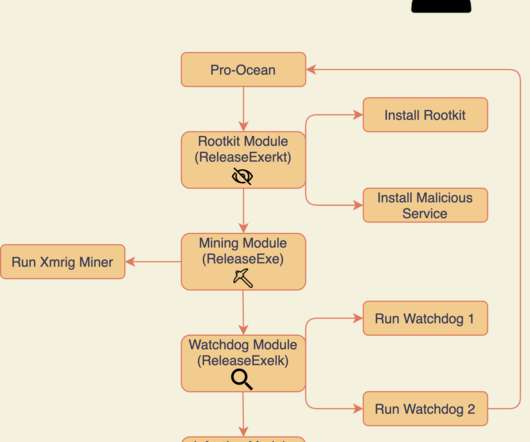
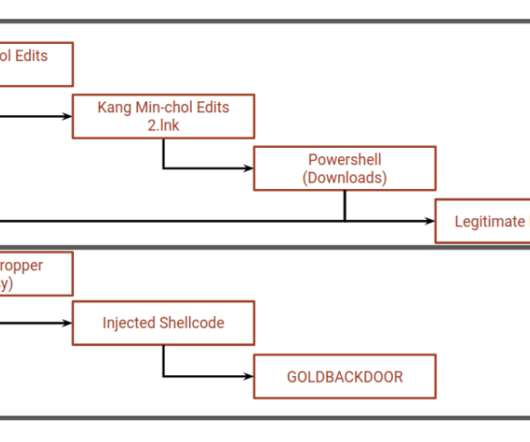

































Let's personalize your content