Pegasus Project – how governments use Pegasus spyware against journalists
Security Affairs
JULY 19, 2021
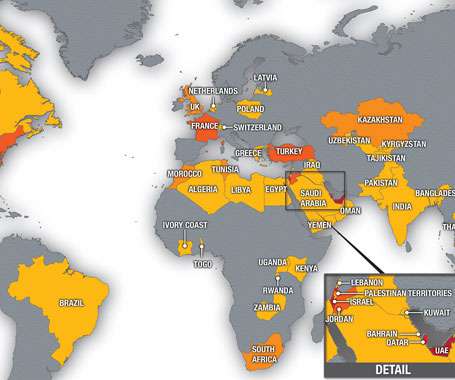
Pegasus is a surveillance malware developed by the Israeli surveillance NSO Group that could infect both iPhones and Android devices, it is sold exclusively to the governments and law enforcement agencies. The evidence demonstrates that governments used Pegasus to intimidate journalists and critical media. Pierluigi Paganini.



































Let's personalize your content