Multifactor Authentication Bypass Attacks: Top Defenses
Data Breach Today
APRIL 22, 2024
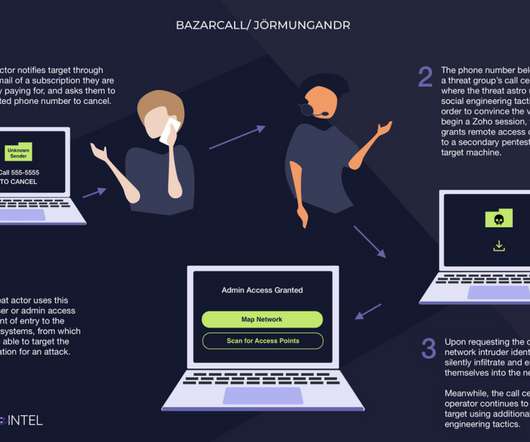
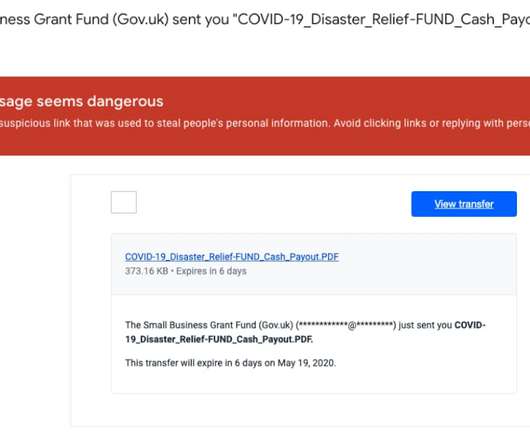
Joe Toomey of Cyber Insurer Coalition Details Rise in Attacks Targeting Weak MFA Adversaries seeking easy access to enterprise networks continue to probe for weak multifactor authentication deployments, oftentimes via nontargeted attacks that lead to phishing pages designed to steal one-time codes, said Joe Toomey, head of security engineering at cyber (..)














































Let's personalize your content