How to Tackle the Information Management Challenges of Legacy Applications
AIIM
SEPTEMBER 3, 2020
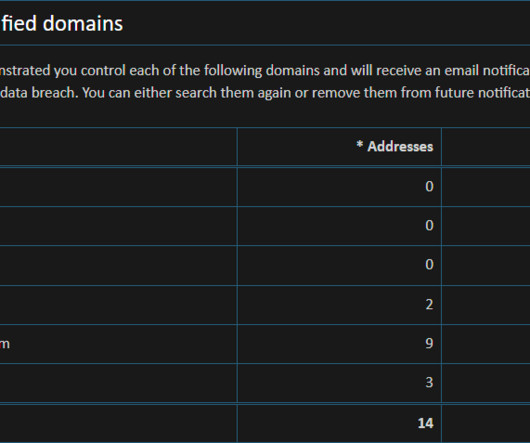
Many organizations feel forced to keep legacy applications alive to retain access to historical data – either for customer service, operational requirements, or compliance. A smarter alternative is decommissioning those legacy applications and extracting important historical data to a searchable repository, accessible for business use.

































Let's personalize your content