FBI, CISA Echo Warnings on ‘Vishing’ Threat
Krebs on Security
AUGUST 21, 2020
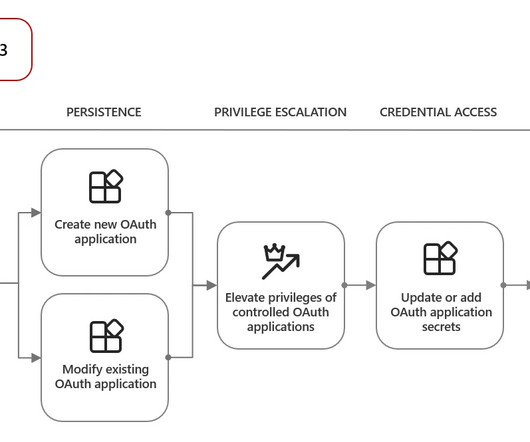
“In mid-July 2020, cybercriminals started a vishing campaign—gaining access to employee tools at multiple companies with indiscriminate targeting — with the end goal of monetizing the access.” Restrict VPN access hours, where applicable, to mitigate access outside of allowed times.







































Let's personalize your content