FritzFrog P2P Botnet is back and targets Healthcare, Education and Government Sectors
Security Affairs
FEBRUARY 11, 2022
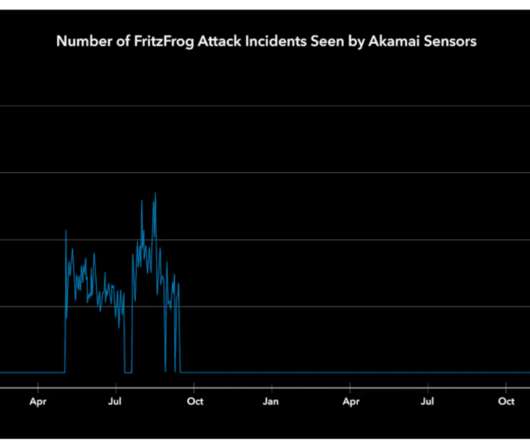
FritzFrog P2P botnet is back and is targeting servers belonging to entities in the healthcare, education, and government sectors. The bot is written in Golang and implements wormable capabilities, experts reported attacks against entities in the government, education, and finance sectors. Pierluigi Paganini.









































Let's personalize your content