Over 400 Cyberattacks at US Public Schools in 2020
Data Breach Today
MARCH 15, 2021
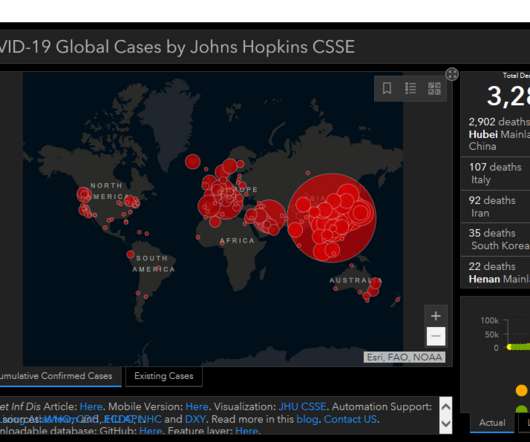
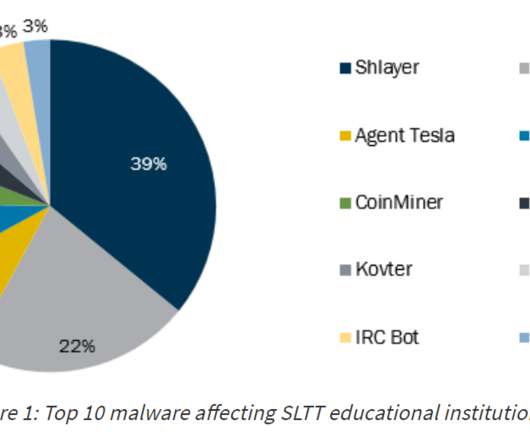
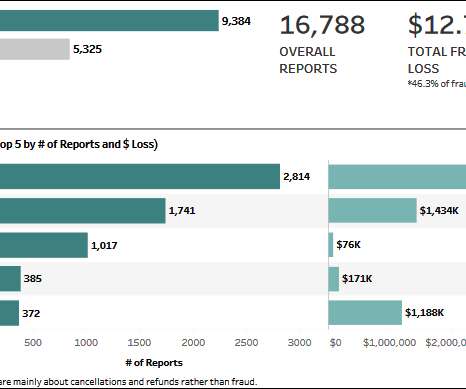
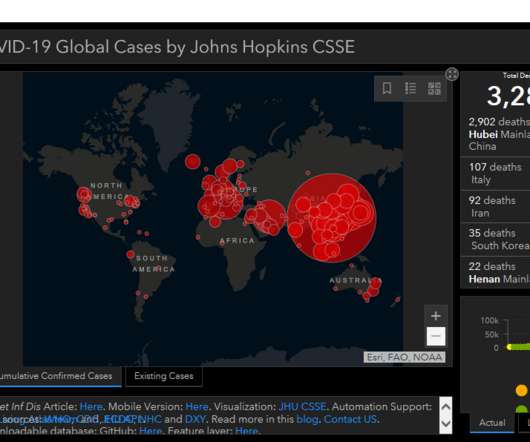
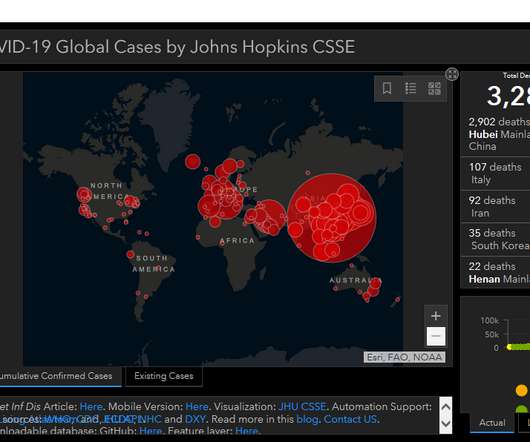
public schools faced a record number of cyber incidents in 2020, with over 400 attacks reported. This led to a spike in school cancellations, as IT staff members struggled to get systems back online while dealing with the COVID-19 pandemic, reports the K-12 Cybersecurity Resource Center.









































Let's personalize your content