IoT devices at major Manufacturers infected with crypto-miner
Security Affairs
FEBRUARY 8, 2020
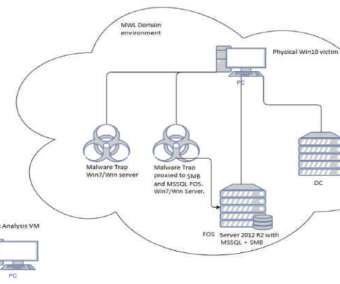
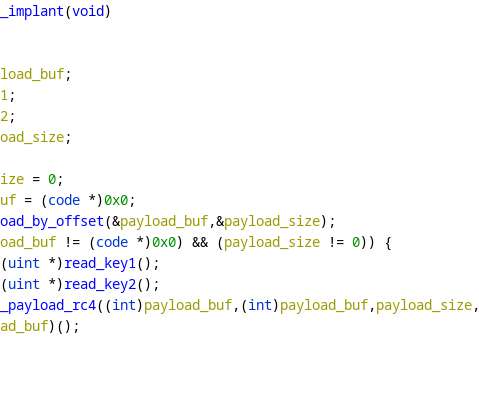
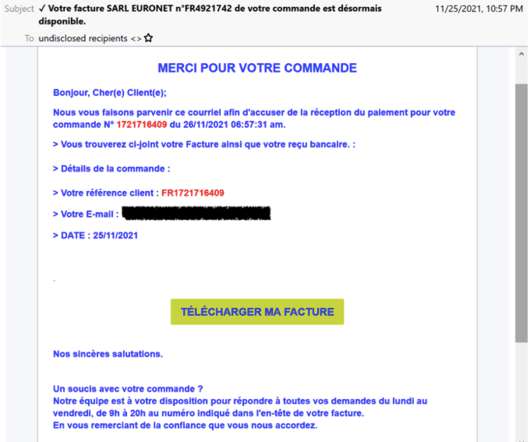
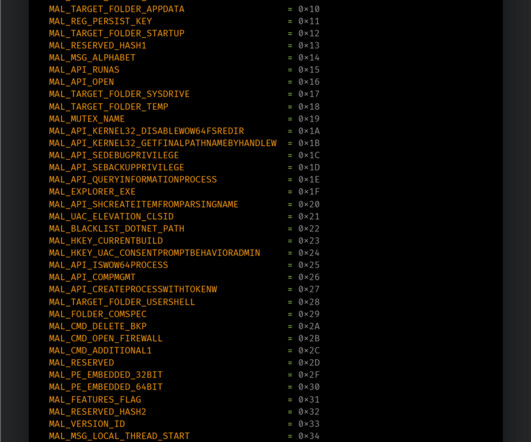
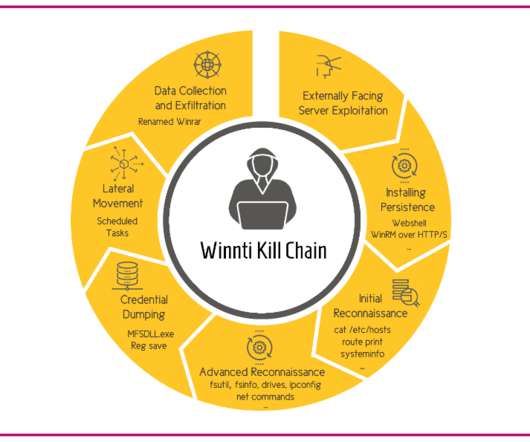
Hackers have infected with a piece of malware some IoT devices running Windows 7 designed by three of the world’s largest manufacturers. The experts reported that several IoT devices at some major manufacturers have been infected with a cryptocurrency miner in October 2019. ” reads the report p ublished by TrapX.”First,




































Let's personalize your content