A zero-day exploit for Log4j Java library could have a tsunami impact on IT giants
Security Affairs
DECEMBER 10, 2021
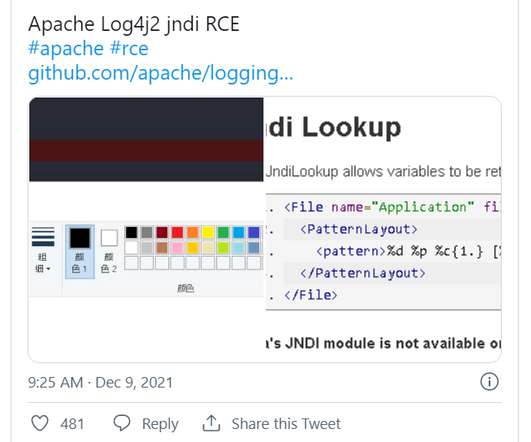
Experts publicly disclose Proof-of-concept exploits for a critical zero-day vulnerability in the Apache Log4j Java-based logging library. Experts publicly disclose Proof-of-concept exploits for a critical remote code execution zero-day vulnerability, tracked a CVE-2021-44228 (aka Log4Shell ), in the Apache Log4j Java-based logging library.












































Let's personalize your content