British Library suffers major outage due to cyberattack
Security Affairs
NOVEMBER 1, 2023
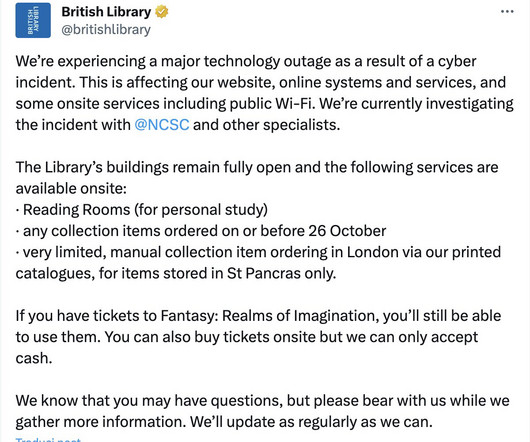
Last weekend, the British Library suffered a cyberattack that caused a major IT outage, impacting many of its services. The British Library is facing a major outage that impacts the website and many of its services following a cyber attack that took place on October 28. ” reads a tweet published by the library. .”







































Let's personalize your content