El Chapo's Encryption Defeated by Turning His IT Consultant
Schneier on Security
JANUARY 16, 2019
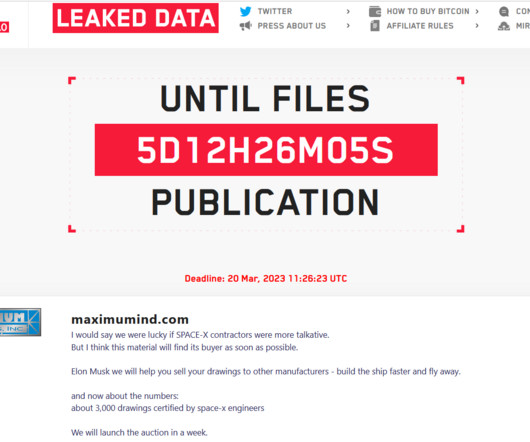
his system's secret encryption keys in 2011 after he had moved the network's servers from Canada to the Netherlands during what he told the cartel's leaders was a routine upgrade. Impressive police work : In a daring move that placed his life in danger, the I.T. consultant eventually gave the F.B.I.







































Let's personalize your content