YTStealer info-stealing malware targets YouTube content creators
Security Affairs
JUNE 29, 2022
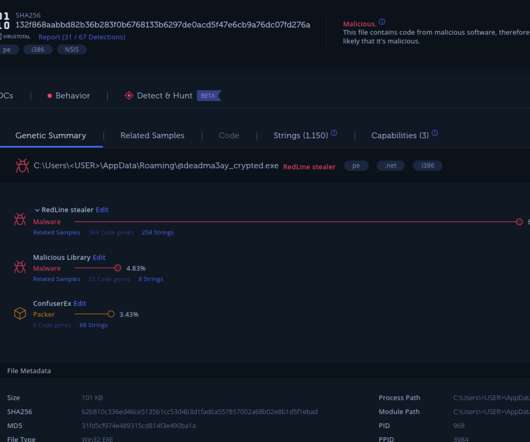
To control the browser, the malware uses a library called Rod. The malware encrypts all the data with a key that is unique for each sample and sends it along with a sample identifier to the C2 server located at the domain name youbot[.]solutions. Aparat is an Iranian video-sharing site that was founded in 2011.















Let's personalize your content