Why is ‘Juice Jacking’ Suddenly Back in the News?
Krebs on Security
APRIL 14, 2023
KrebsOnSecurity received a nice bump in traffic this week thanks to tweets from the Federal Bureau of Investigation (FBI) and the Federal Communications Commission (FCC) about “ juice jacking ,” a term first coined here in 2011 to describe a potential threat of data theft when one plugs their mobile device into a public charging kiosk.










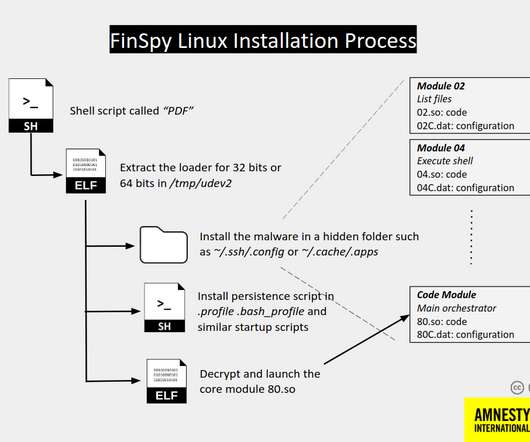


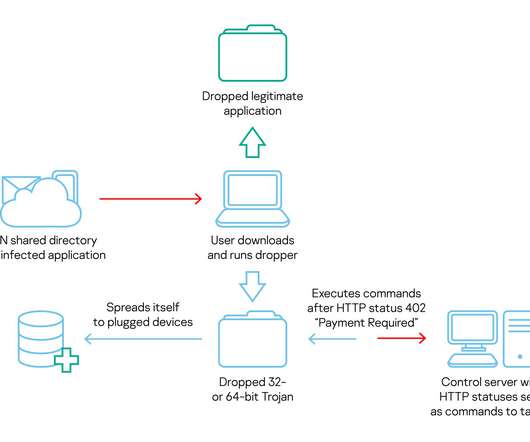



























Let's personalize your content