KashmirBlack, a new botnet in the threat landscape that rapidly grows
Security Affairs
OCTOBER 26, 2020
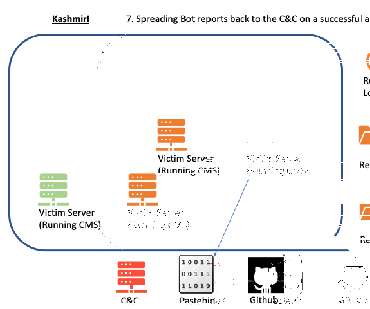
It handles hundreds of bots, each communicating with the C&C to receive new targets, perform brute force attacks, install backdoors, and expand the size of the botnet.” The experts observed millions of attacks per day on average, on thousands of victims in more than 30 different countries around the world.














Let's personalize your content