Security Vulnerabilities in Covert CIA Websites
Schneier on Security
OCTOBER 1, 2022
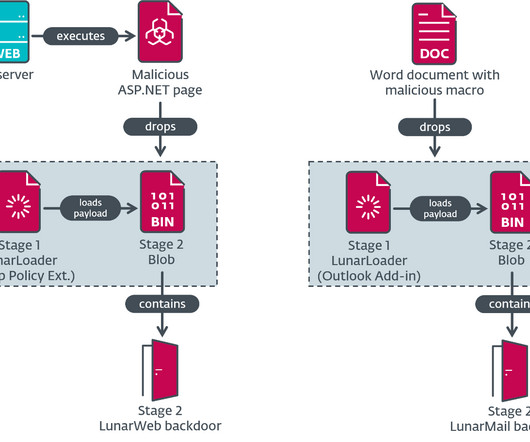
Back in 2018, we learned that covert system of websites that the CIA used for communications was compromised by —at least—China and Iran, and that the blunder caused a bunch of arrests, imprisonments, and executions. The bulk of the websites that we discovered were active at various periods between 2004 and 2013.







































Let's personalize your content