Hatch Bank data breach caused by the exploitation of the GoAnywhere MFT zero-day
Security Affairs
MARCH 6, 2023
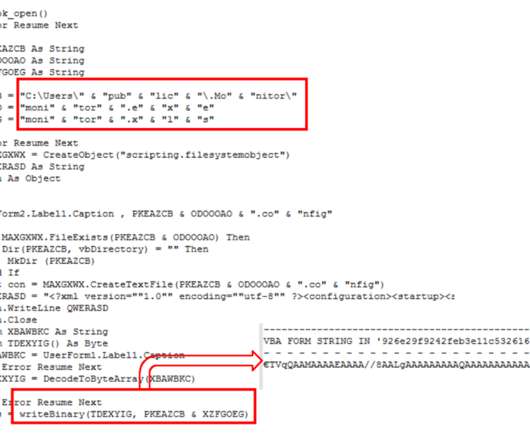
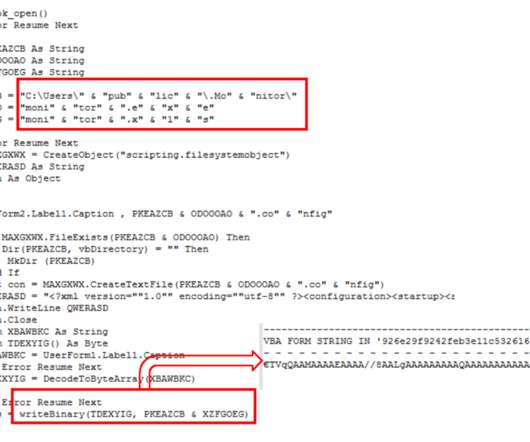
Fintech platform Hatch Bank disclosed a data breach, hackers exploited a recently discovered zero-day in Fortra GoAnywhere MFT secure file-sharing platform. Hatch Bank immediately took steps to secure its files and then launched a diligent and comprehensive review of relevant files to determine the information that may have been impacted.













































Let's personalize your content