New skimmer attack uses WebSockets to evade detection
Security Affairs
NOVEMBER 15, 2020
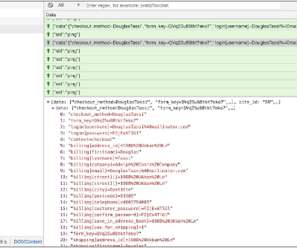
“Online stores are increasingly outsourcing their payment processes to third-party vendors, which means that they don’t handle credit card data inside their store. Once executed, a malicious JavaScript file is requested from the a C2 server (at https[:]//tags-manager[.]com/gtags/script2 com/gtags/script2 ).































Let's personalize your content