China-linked threat actors are targeting the government of Ukraine
Security Affairs
MARCH 18, 2022
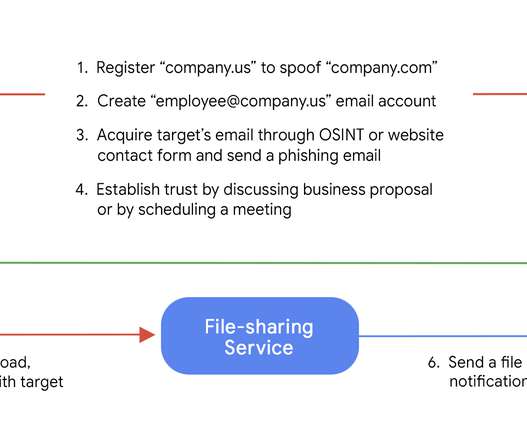
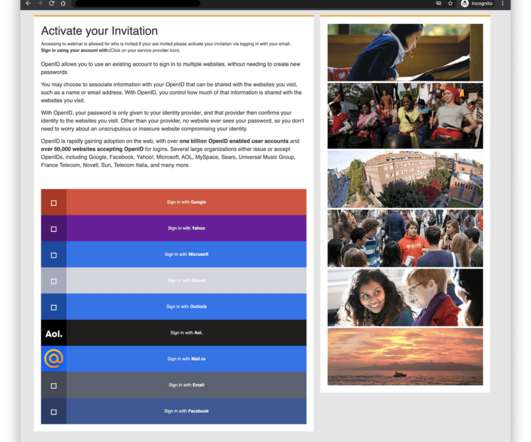
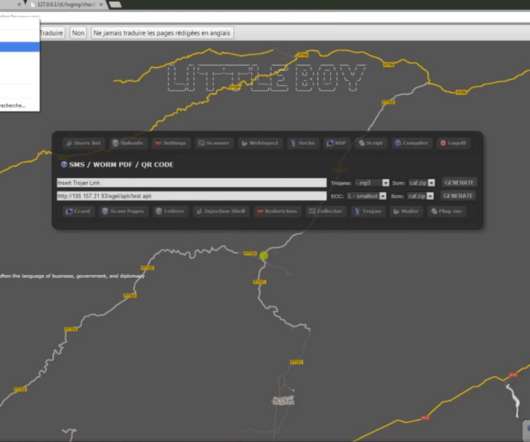
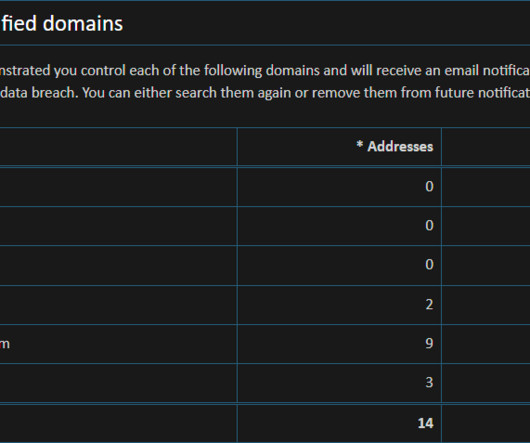
Google’s TAG team revealed that China-linked APT groups are targeting Ukraine’s government for intelligence purposes. Below is the tweet published by TAG chief, Shane Huntley, who cited the Google TAG Security Engineer Billy Leonard. ” wrote Leonard. link] — Shane Huntley (@ShaneHuntley) March 15, 2022.








































Let's personalize your content