Hacker Exploits Months-Old Bug to Steal Crypto From ATMs
Data Breach Today
MARCH 20, 2023
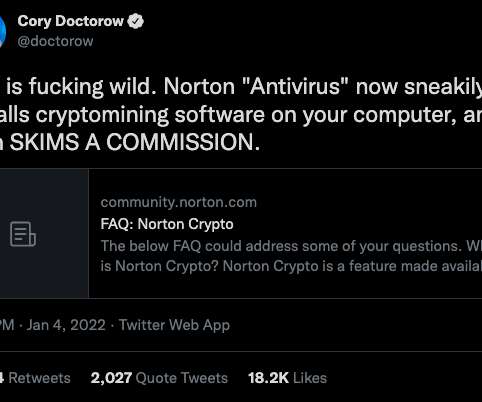
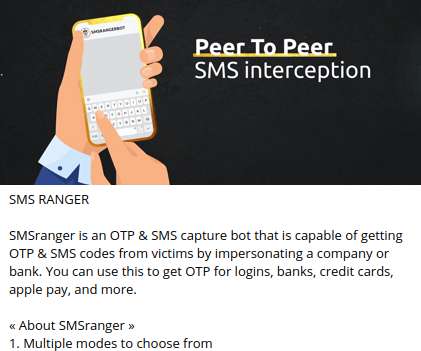
Now-Patched Bug Allowed Thief to Remotely Steal User Passwords, Private Keys Bitcoin ATM manufacturer General Bytes suspended its cloud services supporting more than 15,000 machines after a hacker exploited a vulnerability in its software to steal user passwords and private keys and made off with cryptocurrency worth millions of dollars.












































Let's personalize your content