Sale of 4 Million Stolen Cards Tied to Breaches at 4 Restaurant Chains
Krebs on Security
NOVEMBER 26, 2019
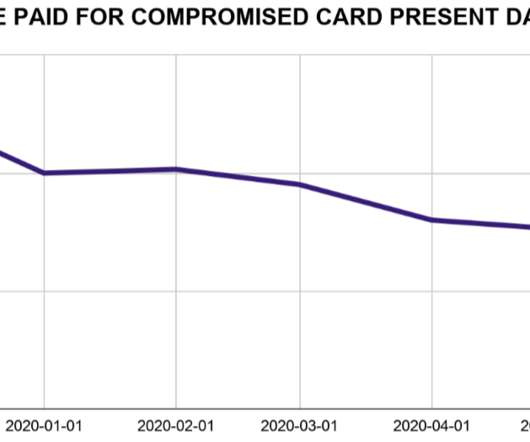
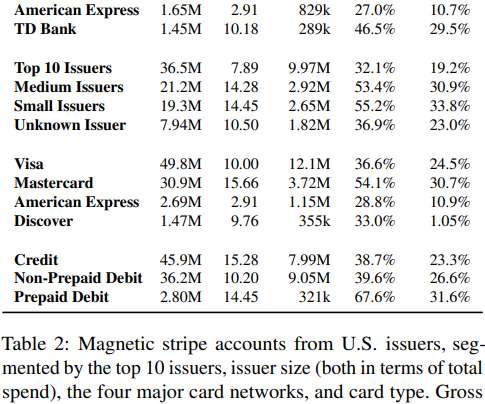
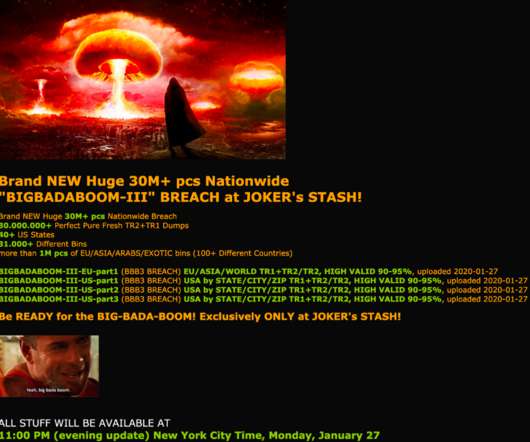
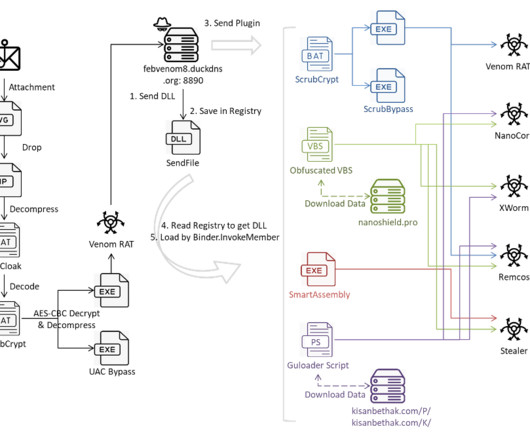
The stolen cards went up for sale at the infamous Joker’s Stash carding bazaar. This type of point-of-sale malware is capable of copying data stored on a credit or debit card’s magnetic stripe when those cards are swiped at compromised payment terminals, and that data can then be used to create counterfeit copies of the cards.







































Let's personalize your content