Previously undetected Earth Longzhi APT group is a subgroup of APT41
Security Affairs
NOVEMBER 15, 2022
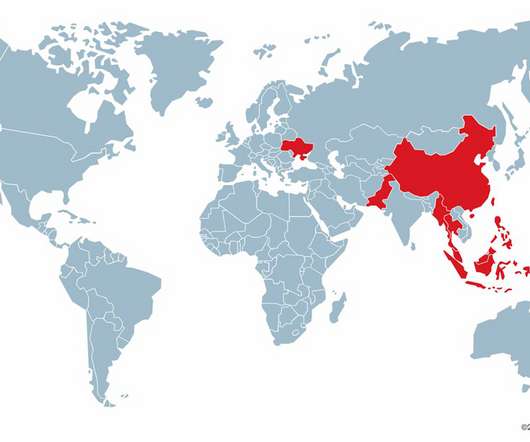
Early this year, Trend Micro investigated a security breach suffered by a company in Taiwan. The second campaign from 2021 to 2022, targeted high-profile victims in the defense, aviation, insurance, and urban development industries in Taiwan, China, Thailand, Malaysia, Indonesia, Pakistan, and Ukraine. . ” concludes the report.

























Let's personalize your content