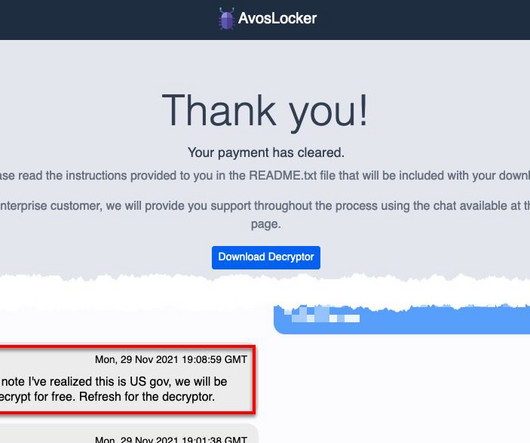
FBI and CISA published a new advisory on AvosLocker ransomware
Security Affairs
OCTOBER 13, 2023
This joint CSA updates the advisory published by the US Government on March 17, 2022. AvosLocker affiliates use legitimate software and open-source remote system administration tools to compromise the victims’ networks. Scripts to execute legitimate native Windows tools [T1047], such as PsExec and Nltest.













































Let's personalize your content