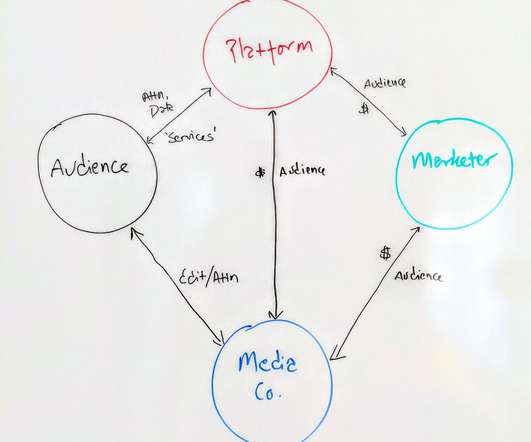
What is Integrated Business Planning (IBP)?
IBM Big Data Hub
JUNE 29, 2023
A retail company experiences a sudden surge in online sales due to a viral social media campaign. By having real-time data at their fingertips, decision-makers can adjust their strategies, allocate resources accordingly, and capitalize on the unexpected spike in demand, ensuring customer satisfaction while maximizing revenue.








































Let's personalize your content