INFRA:HALT flaws impact OT devices from hundreds of vendors
Security Affairs
AUGUST 4, 2021
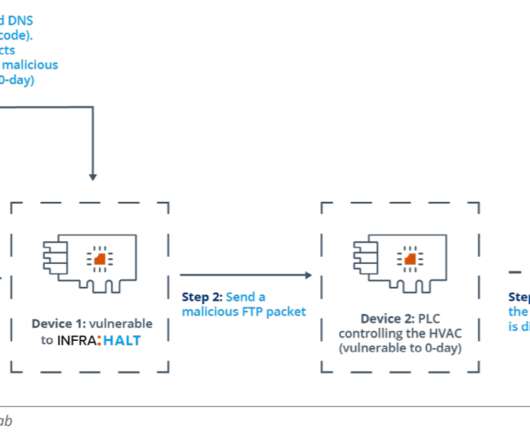
IN FRA:HALT is a set of vulnerabilities affecting a popular TCP/IP library commonly OT devices manufactured by more than 200 vendors. In fact, INFRA:HALT includes examples of memory corruption like in AMNESIA:33, weak ISN generation like in NUMBER:JACK and DNS vulnerabilities like in NAME:WRECK” continues the report.















































Let's personalize your content