FIN7 targeted a large U.S. carmaker phishing attacks
Security Affairs
APRIL 18, 2024
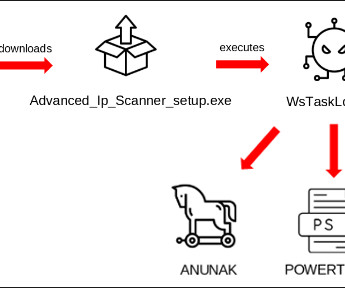
In late 2023, BlackBerry researchers spotted the threat actor FIN7 targeting a large US automotive manufacturer with a spear-phishing campaign. BlackBerry reported that the financially motivated group FIN7 targeted the IT department of a large U.S. carmaker with spear-phishing attacks.




































Let's personalize your content