Hackers hijacked the eScan Antivirus update mechanism in malware campaign
Security Affairs
APRIL 24, 2024
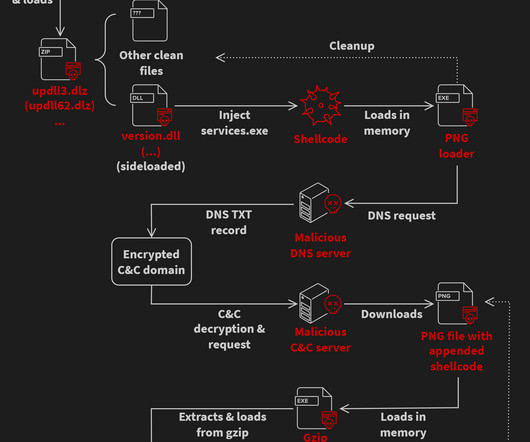
The issue in the update mechanism was present for at least five years. Below the infection chain described by Avast: The eScan updater triggers the update The downloaded package file is replaced with a malicious one on the wire because of a missing HTTPS encryption (MitM is performed) A malicious package updll62.dlz








































Let's personalize your content