UK: New National Strategy for Health Data
DLA Piper Privacy Matters
JULY 13, 2022
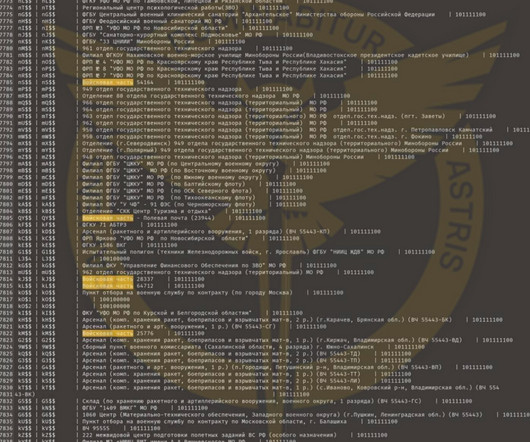
The UK’s Department for Health and Social Care (“ DHSC ”) has published a major strategy document (‘ Data saves lives: reshaping health and social care with data ’) outlining the government’s plans for the regulation and use of data in healthcare. Secure data environments are a hot topic in data circles.















































Let's personalize your content