Navigating Compliance: Understanding India's Digital Personal Data Protection Act
Thales Cloud Protection & Licensing
MAY 8, 2024
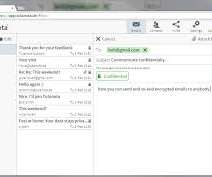
Navigating Compliance: Understanding India's Digital Personal Data Protection Act madhav Thu, 05/09/2024 - 05:30 In August 2023, the Indian Parliament passed a piece of landmark legislation, the Digital Personal Data Protection (DPDP) Act, marking a significant shift in India's data protection landscape.
















































Let's personalize your content