Probing Marriott's Mega-Breach: 9 Cybersecurity Takeaways
Data Breach Today
NOVEMBER 10, 2020
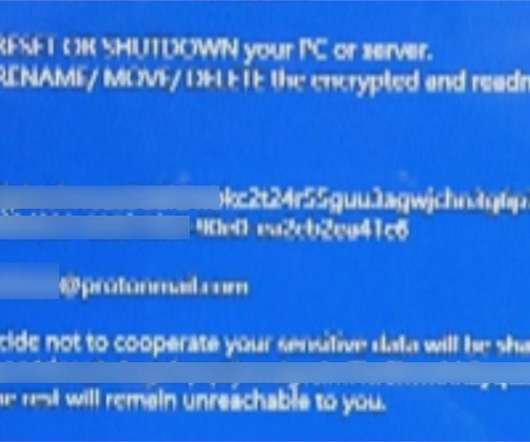
Investigators Find Encryption, Monitoring, Logging and Whitelisting Failures Inadequate database and privileged account monitoring, incomplete multi-factor authentication and insufficient use of encryption: Britain's privacy regulator has cited a raft of failures that contributed to the four-year breach of the Starwood guest reservation system discovered by Marriott in 2018.




































Let's personalize your content