11 Cybersecurity Vendors to Watch in 2021
Dark Reading
JUNE 10, 2021
The cybersecurity landscape continues to spawn new companies and attract new investments. Here is just a sampling of what the industry has to offer.

Dark Reading
JUNE 10, 2021
The cybersecurity landscape continues to spawn new companies and attract new investments. Here is just a sampling of what the industry has to offer.

Micro Focus
JUNE 9, 2021
Technology can play a key role in helping to reduce an organization’s environmental impact. At Micro Focus, our aim is to make sustainable and responsible business part of the way we operate. From lowering our energy consumption and waste materials, to helping our customers address their carbon footprint and adopt carbon friendly IT strategies –.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

WIRED Threat Level
JUNE 6, 2021
It's a growing threat for individual users and businesses alike—but there are ways to protect yourself.

Data Breach Today
JUNE 5, 2021
Dr. Claudia Natanson Describes Vision of U.K.’s New Self-Regulatory Body U.K. Cyber Security Council is a new self-regulatory body for the profession. It is tasked by the U.K. Government to execute their vision for the U.K. to be one of the safest places to work and do business online, says the chair of the Council’s Board of Trustees, Dr. Claudia Natanson.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Krebs on Security
JUNE 8, 2021
Microsoft today released another round of security updates for Windows operating systems and supported software, including fixes for six zero-day bugs that malicious hackers already are exploiting in active attacks. June’s Patch Tuesday addresses just 49 security holes — about half the normal number of vulnerabilities lately. But what this month lacks in volume it makes up for in urgency: Microsoft warns that bad guys are leveraging a half-dozen of those weaknesses to break into comp
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Matters
JUNE 11, 2021
On June 2, 2021, Nevada Governor Steve Sisolak signed SB260 , a bill that will amend the state’s existing privacy notice legislation, NRS 603A.300 to.360 (“Existing NV Privacy Law”). SB260 amends the Existing NV Privacy Law by exempting certain persons and information collected about a consumer from the law’s privacy requirements, expanding the types of entities that must facilitate consumer privacy opt-out rights, providing new and updated definitions, authorizing the opportunity to remedy a fa

Data Breach Today
JUNE 10, 2021
New Stand-Alone Firm Is Tasked With Combatting Digital Commerce Fraud RSA Security LLC has spun off its fraud and risk intelligence business into a stand-alone company named Outseer. The new company will be led by Reed Taussig as CEO, and it will serve a worldwide customer and partner community.

Troy Hunt
JUNE 9, 2021
I've had a couple of cases to date where email addresses compromised by malware then discovered in the course of investigations have been provided to Have I Been Pwned (HIBP). Firstly by the Estonian Central Criminal Police a few years ago , then by the FBI and global counterparts this April and now, in the third such case, by NordLocker. (Full disclosure: I'm a strategic advisor for NordVPN who shares the same parent company.

AIIM
JUNE 10, 2021
As late as 2010, many end-users and solution providers viewed SharePoint as useful for project groups and document sharing – but more of an interesting tangent to the world of content management than “real” ECM. However, standalone ECM solutions at that time came at a very high cost. Many of these ECM solutions were built for high-volume scanning/capture applications and priced accordingly.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Security Affairs
JUNE 6, 2021
The REvil ransomware operators said in an interview on the “Russian OSINT” Telegram channel that they accidentally targeted United States-based firms. The recent attack against JBS Foods conducted by REvil ransomware gang (aka Sodinokibi) triggered the response of US authorities, US DoJ announced its decision to equate investigations into ransomware attacks with investigations into terrorism in the wake of the recent hacks.

Data Breach Today
JUNE 7, 2021
Decision to Pay Highlights Healthcare Sector Challenges The recent decision by a Massachusetts-based hospital to pay a ransom in exchange for promises by the attackers to destroy stolen data spotlights the difficult choices many healthcare entities face in the wake of cyberattacks.

Troy Hunt
JUNE 5, 2021
This week has been absolutely dominated by code contributions to Pwned Passwords. This is such an awesome, humbling experience that so many people have wanted to contribute their time to something that makes online life better for all of us. The challenge I have now is, as expected, managing the pull requests, reviewing code and ensuring the project heads in the right direction as support for ingesting the FBI -provided passwords is built out.

Schneier on Security
JUNE 11, 2021
For three years, the Federal Bureau of Investigation and the Australian Federal Police owned and operated a commercial encrypted phone app, called AN0M, that was used by organized crime around the world. Of course, the police were able to read everything — I don’t even know if this qualifies as a backdoor. This week, the world’s police organizations announced 800 arrests based on text messages sent over the app.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Security Affairs
JUNE 10, 2021
Google this week addressed 14 vulnerabilities in the Chrome browser, including a zero-day flaw that has been exploited in the wild. Google released security updates to address 14 vulnerabilities in the Chrome browser, including a zero-day issue that has been exploited in the wild. The most severe of these flaws, tracked as CVE-2021-30544, is a critical use-after-free issue that impacts BFCache.
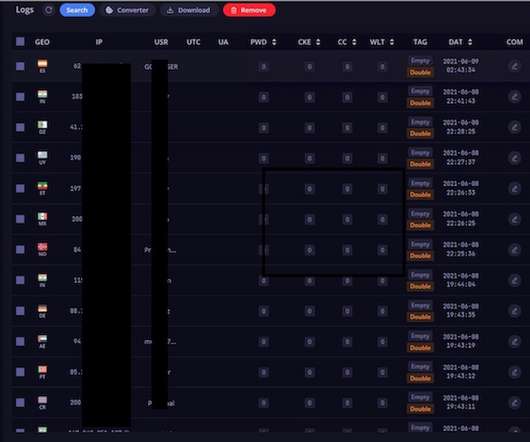
Data Breach Today
JUNE 10, 2021
Data Includes 1.5M Facebook Passwords, Valid Cookies Some 26 million passwords were exposed in a 1.2 terabyte batch of data found by NordLocker, a security company. It's workaday botnet data but highlights a hostile malware landscape, particularly for people still inclined to download pirated software.

Troy Hunt
JUNE 8, 2021
Ever notice how there was a massive gap of almost 9 months between announcing the intention to start open sourcing Have I Been Pwned (HIBP) in August last year and then finally a couple of weeks ago, actually taking the first step with Pwned Passwords ? Many people certainly noticed the time because I kept getting asked when it was actually going to happen.

Threatpost
JUNE 11, 2021
"We hereby keep a right (sic) to forward all of the relevant documentation and data to military agencies of our choise (sic)" REvil reportedly wrote.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Security Affairs
JUNE 7, 2021
Cybercriminals in Russian underground forums have been invited to take part in competitions for hacking cryptocurrency and NFT. Several Russian underground forums have launched competitions for hacking cryptocurrency schema and Non-fungible token (NFT). “Over the past month, operators of one of the top Russian-language cybercrime forums have been running a “contest,” calling for the community to submit papers that examine how to target cryptocurrency-related technology.” reads a post
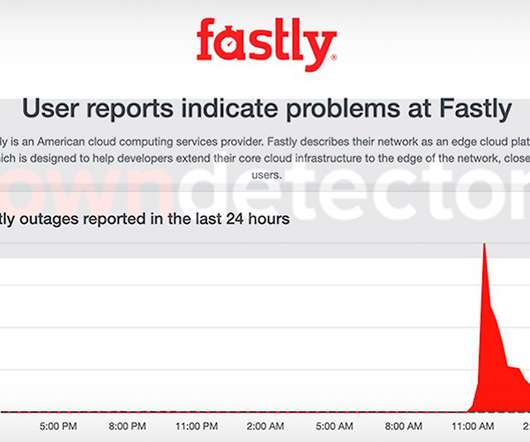
Data Breach Today
JUNE 8, 2021
Access to Amazon, Google, Twitter and Others Disrupted by Content Delivery Network Amazon, Google, Spotify and Twitter were among the sites that were unreachable Tuesday morning due to a configuration error at widely used content delivery network Fastly, which said the problem was resolved after about an hour, after which the disruptions would begin to abate.

Troy Hunt
JUNE 7, 2021
This week as part of the ongoing initiative to make breach data available to national governments, I'm very happy to welcome the national CERT of Uruguay, CERTuy. They are now the 2nd Latin American country and 20th country worldwide to have free and easy API level access to all their government domains. I'm going to continue onboarding governments as they reach out and ask for access, my hope being that greater visibility to the impact of data breaches helps minimise the disruption they cause t

Schneier on Security
JUNE 10, 2021
“Markpainting” is a clever technique to watermark photos in such a way that makes it easier to detect ML-based manipulation: An image owner can modify their image in subtle ways which are not themselves very visible, but will sabotage any attempt to inpaint it by adding visible information determined in advance by the markpainter. One application is tamper-resistant marks.

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Security Affairs
JUNE 11, 2021
The Avaddon ransomware gang has shut down its operations and released the decryption keys to allow victims to recover their files for free. Good news for the victims of the Avaddon ransomware gang , the cybercrime group has shut down its operations and provided the decryption keys to BleepingComputer website. The group has also shut down its servers and deleted profiles on hacking forums, they also shut down their leak site.

Data Breach Today
JUNE 8, 2021
Complaint Alleged Multiple Security 'Failures' Leading to 2020 Cyberattack A federal court has approved a proposed settlement in a class action lawsuit filed in February against Nebraska Medicine in the wake of a 2020 malware attack and exfiltration of sensitive personal and health data for tens of thousands of individuals.

Threatpost
JUNE 10, 2021
The decision to pay the ransom demanded by the cybercriminal group was to avoid any further issues or potential problems for its customers, according to the company’s CEO.

Jamf
JUNE 11, 2021
Following a year unlike any other, Apple’s Worldwide Developer Conference (WWDC) wrapped up this week with news for enterprise IT, InfoSec leaders, and education IT professionals alike.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
Security Affairs
JUNE 5, 2021
Cyble researchers investigated a recent attack on an India-based IT firm that was hit by the BlackCocaine Ransomware gang. Recently Cyber researchers for Cyble investigated an attack suffered by on May 30, 2021, by Nucleus Software, an India-based IT company in the Banking and Financial Services sector. The company reported the security breach to the Bombay Stock Exchange (BSE) and the National Stock Exchange of India (NSEI).

Data Breach Today
JUNE 11, 2021
Experts Say Odd Case Offers Forewarning to Others The chief operating officer of a network security firm serving the healthcare sector has been charged by federal prosecutors with crimes stemming from an alleged cyberattack on an Atlanta, Georgia-area medical center in 2018. Some legal experts say the unusual case offers forewarnings to others.

Data Matters
JUNE 5, 2021
The European Commission ( EC ) on June 4, 2021 adopted a new set of Standard Contractual Clauses for international data transfers ( New SCCs ). The New SCCs take into account the Court of Justice of the European Union’s ( CJEU ) decision in Schrems II , requirements under the EU General Data Protection Regulation ( GDPR ), and according to the EC “address the realities faced by modern business”.
Let's personalize your content