Phishing Personified
Dark Reading
FEBRUARY 6, 2020
What makes these scams so completely obvious in the physical form?

Dark Reading
FEBRUARY 6, 2020
What makes these scams so completely obvious in the physical form?

WIRED Threat Level
FEBRUARY 6, 2020
The nation’s first primary is proudly low-tech, but it'll take more than paper ballots to defuse the disinformation threat.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Matters
FEBRUARY 6, 2020
The U.S. Securities and Exchange Commission’s Office of Compliance Inspections and Examinations (OCIE) released a report on Cybersecurity and Resiliency Observations based on practices seen in prior exams. OCIE published the overview of practices to help market participants when considering “how to enhance cybersecurity preparedness and operational resiliency,” while acknowledging that there is not a “one-size fits all” approach.

Data Breach Today
FEBRUARY 6, 2020
Inquiry Posing Interview Questions Designed to Steal Credentials In a recently discovered phishing campaign, hackers attempted to steal victims' passwords and credentials by posing as a former Wall Street Journal reporter and sending documents with potential interview questions, according to security firm Certfa.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.
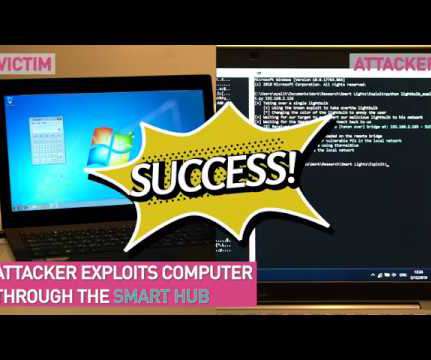
Security Affairs
FEBRUARY 6, 2020
Check Point experts discovered a high-severity flaw in Philips Hue Smart Light Bulbs that can be exploited to gain entry into a targeted WiFi network. Security experts from Check Point discovered a high-severity flaw ( CVE-2020-6007 ) in Philips Hue Smart Light Bulbs that can be exploited by hackers to gain entry into a targeted WiFi network. Lightbulbs could be remotely controlled through a mobile app or via a digital home assistant, owners could control the light in the environment and even
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
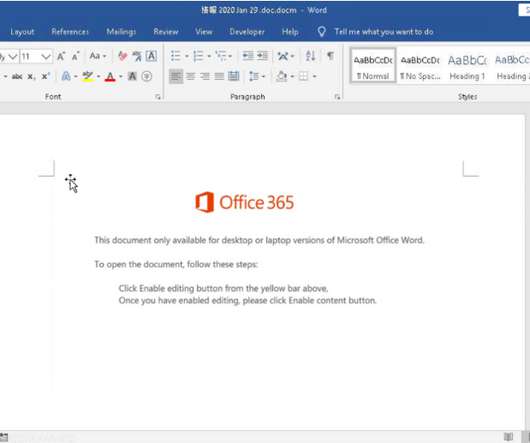
IT Governance
FEBRUARY 6, 2020
Cyber criminals are exploiting the public’s fear of the Wuhan in a new phishing scam , researchers have learned. Experts at IBM discovered a spate of phishing emails being sent to Japanese citizens, asking them to open an attached Word document supposedly containing details of infections in the country’s main island. The email reads: Department of Health Services.

Data Breach Today
FEBRUARY 6, 2020
Stolen Laptop Contained Patient Data on Thousands Just when you thought the days of big data breaches tied to stolen unencrypted laptops were over comes news of an incident in Oregon affecting hundreds of thousands. What happened this time?

AIIM
FEBRUARY 6, 2020
Reaching your Digital Transformation goals often requires the addition of new software solutions. But, shopping around for software can be a challenge. How are organizations expected to fully assess the precision of one software system/solution and compare it to another? Are we expected to become experts on each option? In our personal lives, when we shop for something like a new pair of shoes, we try on different brands and sizes to see what fits best for our needs.

Data Breach Today
FEBRUARY 6, 2020
Move Appears to Be Aimed at Big Data-Scraping Firms Such as Clearview AI Facebook scientists have proposed using "radioactive data" watermarks to identify when online images get used to train neural networks. The proposal appears to be aimed at the rise of big data startups, such as Clearview AI, that are scraping publicly available photographs to create facial recognition tools.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Thales Cloud Protection & Licensing
FEBRUARY 6, 2020
Artificial intelligence (AI) is becoming increasingly integral to information security. From the multitude of ways AI is used in business to creating smart cities and safeguarding transportation , AI impacts nearly every aspect of our lives. In fact, in its Reinventing Cybersecurity with Artificial Intelligence report , Capgemini found that 61% of respondents said they can no longer detect data breach attempts without the help of AI.

Data Breach Today
FEBRUARY 6, 2020
The coronavirus statistics are dizzying - as of Thursday, there were more than 28,000 infections and about 560 deaths. But the key stat to watch is the mortality rate, currently 2 percent, says pandemic expert Regina Phelps. How that number changes will dictate how business continuity leaders must respond.

Troy Hunt
FEBRUARY 6, 2020
I've got audio! Ok, so I cheated a bit in terms of recording back in the home office, but the plugs I need to make the Zoom H6 work the way it should (and yeah, I know I said "Rode" H6 in the vid, sorry!) are on the way and hopefully they'll be all good for next week when I'm in Sydney. I'm talking about that trip in this week's update along with the Chrome 80 changes to SameSite cookies not that its hit, the Adult FriendFinder breach and then recapping on a heap of the week's news in tweets.

Security Affairs
FEBRUARY 6, 2020
A set of vulnerabilities in the Cisco Discovery Protocol (CDP) exposes tens of millions of devices to the risk of cyber attacks. Researchers at IoT security firm Armis discovered a set of five serious vulnerabilities in the implementation of the Cisco Discovery Protocol (CDP) protocol. The experts tracked the set as CDPwn and warned that the issues could be exploited by attackers to take complete control of vulnerable devices. “ Armis has discovered five critical, zero-day vulnerabilities

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

The Guardian Data Protection
FEBRUARY 6, 2020
Ombudsman says ‘greyness’ in metadata definition must be examined as the practice is excluded in legislation Law enforcement agencies are being provided with the web browsing histories of people under investigation using mandatory data retention powers, despite the federal government specifically excluding that practice in the legislation, the commonwealth ombudsman has warned.

OpenText Information Management
FEBRUARY 6, 2020
Organizations deal with lawsuits all the time – from workplace discrimination, overtime pay, customer injuries sustained on-premises, intellectual property, contracts and more. When litigation looms, organizations have a duty to identify and preserve relevant data that may be evidence to the specific litigation. The purpose is to avoid the intentional or inadvertent destruction of relevant … The post How prepared is your IT department for the next legal hold?

Dark Reading
FEBRUARY 6, 2020
The 10 finalists will each have three minutes to make their case for being the most innovative, promising young security company of the year.

OpenText Information Management
FEBRUARY 6, 2020
The Digital Era is over. We have entered the Information Era. Technological Progress—The Information Era Building on the groundwork of automation, connectivity and computing power that defined digital, the Information Era is characterized by our unprecedented ability to capture, store and make sense of masses of information. By next year, humans will have accumulated around … The post The Information Opportunity appeared first on OpenText Blogs.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Threatpost
FEBRUARY 6, 2020
The powerful Minebridge backdoor gives cyberattackers full run of a victim's machine.
Dark Reading
FEBRUARY 6, 2020
In Iowa this week, a smartphone app for reporting presidential caucus results debuted. It did not go well.

HL Chronicle of Data Protection
FEBRUARY 6, 2020
In today’s connected world, businesses face constant pressure to improve their cybersecurity practices and to confirm that they are meeting industry standards. To continue helping businesses achieve those goals, the SEC Office of Compliance Inspections and Examination (OCIE) published on January 27 its latest Examination Observations related to cybersecurity and operational resiliency practices.

Schneier on Security
FEBRUARY 6, 2020
Jim Sanborn, who designed the Kryptos sculpture in a CIA courtyard, has released another clue to the still-unsolved part 4. I think he's getting tired of waiting. Did we mention Mr. Sanborn is 74? Holding on to one of the world's most enticing secrets can be stressful. Some would-be codebreakers have appeared at his home. Many felt they had solved the puzzle, and wanted to check with Mr.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Dark Reading
FEBRUARY 6, 2020
Businesses receive $30,000 of 'free' CISO time as security leaders report job-related stress taking a toll on their health and relationships.

Privacy and Cybersecurity Law
FEBRUARY 6, 2020
On Friday, January 31, 2020, the United Kingdom (UK) left the European Union (EU) after 47 years as part of the union. While the UK has ceased to be part of the EU when the clock struck midnight in Brussels, the UK and EU have agreed to a transition period until the end of 2020, to allow the UK to continue its current relationship with the EU, while future trading relationships are negotiated.

Threatpost
FEBRUARY 6, 2020
APT group poses as a former Wall Street Journal journalist to launch phishing campaigns and steal victim email account details.

Privacy and Cybersecurity Law
FEBRUARY 6, 2020
On Friday, January 31, 2020, the United Kingdom (UK) left the European Union (EU) after 47 years as part of the union. While the UK has ceased to be part of the EU when the clock struck midnight in Brussels, the UK and EU have agreed to a transition period until the end of 2020, to allow the UK to continue its current relationship with the EU, while future trading relationships are negotiated.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Information Management Resources
FEBRUARY 6, 2020
With big data-as-a-service, tools such as analytics software and storage are delivered via the cloud by a service provider.

Preservica
FEBRUARY 6, 2020
Oxford, UK; Boston, MA February 6, 2020 : Preservica, the market leader in SaaS active digital preservation, is pleased to announce the formation of a new Advisory Council of experienced senior executives. The Council will provide industry, regulatory, information management and technological guidance to the Preservica management team and Board of Directors to support the business in further extending its leadership position and continuing to deliver innovative, best-of-breed digital preservatio

Zapproved
FEBRUARY 6, 2020
We are proud to be part of TechTownPDX, an organization dedicated to fostering diverse and inclusive companies that offer opportunities to all. The post What Does TechTownPDX Membership Mean to Us? appeared first on Zapproved.
Let's personalize your content