Paying Ransomware Paints Bigger Bullseye on Target’s Back
Threatpost
JUNE 8, 2022
Ransomware attackers often strike targets twice, regardless of whether the ransom was paid.

Threatpost
JUNE 8, 2022
Ransomware attackers often strike targets twice, regardless of whether the ransom was paid.

Data Breach Today
JUNE 8, 2022
CISA, FBI and NSA Detail TTPs, Top Exploited Flaws, Mitigation Measures CISA says Chinese state-sponsored threat actors are exploiting known vulnerabilities to target public and private companies in the United States, and a related joint advisory from CISA, the FBI and the NSA describes how major telcos and network service providers have been exploited since 2020.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
JUNE 8, 2022
Black Basta ransomware gang implemented a new feature to encrypt VMware ESXi virtual machines (VMs) running on Linux servers. The Black Basta ransomware gang now supports encryption of VMware ESXi virtual machines (VMs) running on Linux servers. Researchers from Uptycs first reported the discovery of the new Black Basta ransomware variant that supports encryption of VMWare ESXi servers.

Data Breach Today
JUNE 8, 2022
24M US Citizens Listed on SSNDOB Marketplace - But Have All Domains Been Seized? SSNDOB, a darknet marketplace selling stolen Social Security numbers and birthdates, has been shut down, says the U.S. Department of Justice. The takedown was the result of a multiagency effort involving the IRS-CI, the FBI, the DOJ, and law enforcement agencies of Cyprus and Latvia.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Security Affairs
JUNE 8, 2022
China-linked threat actors have breached telecommunications companies and network service providers to spy on the traffic and steal data. US NSA, CISA, and the FBI published a joint cybersecurity advisory to warn that China-linked threat actors have breached telecommunications companies and network service providers. The nation-state actors exploit publicly known vulnerabilities to compromise the target infrastructure. .
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

WIRED Threat Level
JUNE 8, 2022
Using a custom encryption scheme within music notation, Merryl Goldberg and three other US musicians slipped information to Soviet performers and activists known as the Phantom Orchestra.

Data Breach Today
JUNE 8, 2022
Bernardo Vasquez of Palo Alto Networks on Identity Access Management, Zero Trust For CISOs, it's critical to not implement security without first carefully considering the user's experience, says Bernardo Vasquez, advisory CISO in the strategic client practice of Palo Alto Networks. He explains why and discusses other topics, including ZTNA 2.0.

WIRED Threat Level
JUNE 8, 2022
Using a custom encryption scheme within music notation, Merryl Goldberg and three other US musicians slipped information to Soviet performers and activists known as the Phantom Orchestra.

Data Breach Today
JUNE 8, 2022
Peter Gankin of Takeda Shares His Company's Journey What are some challenges of shifting on-premises PAM to the cloud, and how should one go about it? Peter Gankin, head of identity and access management at Takeda, a Japanese multinational pharmaceutical company, shares his views.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
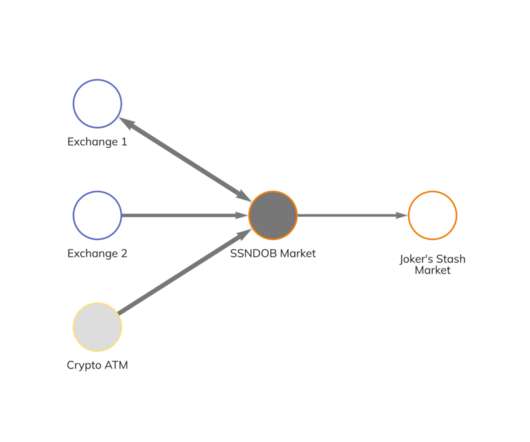
Security Affairs
JUNE 8, 2022
An international operation led by the US authorities dismantled and seized the infrastructure of the online marketplace SSNDOB. US DoJ announced the seizure of the SSNDOB Marketplace, a series of websites offering personal information, including the names, dates of birth, and Social Security numbers belonging to individuals in the United States. According to the authorities, the SSNDOB Marketplace has listed the personal information for approximately 24 million individuals in the United States,

DLA Piper Privacy Matters
JUNE 8, 2022
On 8 March 2022, The Data Protection Act 2018 (Access Modification) (Health) Regulations 2022 (“the 2022 Regulations ”) came into force, revoking and replacing the Data Protection (Access Modification) (Health) Regulations 1989 (the “1989 Regulations ”). The new 2022 Regulations will have an impact on organisations that process health data (i.e. physical and mental health data) and receive data subject access requests (“ DSARs ”) from individuals invoking their data protection rights under Artic

Collibra
JUNE 8, 2022
I am excited to announce the launch of The Data Download , Collibra’s first ever podcast series. When the marketing team first came to me with this idea, I was thrilled to be part of the project, but I never imagined I would be this passionate about my role as podcast host. . I had never hosted a podcast before and I really did not know what to expect.

Dark Reading
JUNE 8, 2022
The new ransomware strain Black Basta is now actively targeting VMware ESXi servers in an ongoing campaign, encrypting files inside a targeted volumes folder.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Security Affairs
JUNE 8, 2022
0patch researchers released an unofficial security patch for a Windows zero-day vulnerability dubbed DogWalk. 0patch released an unofficial security patch for a new Windows zero-day vulnerability in the Microsoft Support Diagnostic Tool (MSDT) dubbed DogWalk. The issue impacts all Windows versions, starting from Windows 7 and Server Server 2008, including the latest releases.

Data Protection Report
JUNE 8, 2022
On Friday, June 3, 2022, the Senate and House released a draft of the American Data Privacy and Protection Act, ( ADPPA ), a watershed privacy bill that would introduce a federal standard. Currently, a hodgepodge of industry-specific and state laws make up the backbone of American privacy regulations and rights, so a national framework for privacy would establish a uniform system for this core American right.

KnowBe4
JUNE 8, 2022
The US Cybersecurity and Infrastructure Security Agency (CISA) and its partners have issued a joint alert on Karakurt , a data theft extortion group that harasses victims’ employees, customers, and business partners in order to pressure the victim to pay up.
eSecurity Planet
JUNE 8, 2022
As part of our testing and review of Rapid7 InsightIDR , we looked at the SIEM product’s functionality and ease of use in our lab environment. InsightIDR has SIEM at its foundation and scales out to essentially be an XDR solution covering endpoints , network traffic analysis , UEBA , incident response and more. We found InsightIDR to be relatively easy to install.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Threatpost
JUNE 8, 2022
The novel cybercriminal group tapped the ever-evolving info-stealing trojan to move laterally on a network in a recent attack, researchers have found.

Dark Reading
JUNE 8, 2022
Physical access matters in keeping people and buildings safe. Points to consider when establishing a physical security protocol are ways to lock down an area to keep people safe, approaches to communicate clear safety directions, and access control.

Schneier on Security
JUNE 8, 2022
People are leaking classified military information on discussion boards for the video game War Thunder to win arguments — repeatedly.

Dark Reading
JUNE 8, 2022
Anjuna Security's Ayal Yogev joins Dark Reading's Terry Sweeney at Dark Reading News Desk during RSA Conference to discuss how confidential computing will improve cloud security.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Jamf
JUNE 8, 2022
See how iPad programs can help universities improve student engagement, wellness and career readiness.

Dark Reading
JUNE 8, 2022
Compromised routers, VPNs, and NAS devices from Cisco, Citrix, Pulse, Zyxel, and others are all being used as part of an extensive cyber espionage campaign.

eDiscovery Daily
JUNE 8, 2022
By: Julia Romero-Peter, Esq. Information requested from a government agency through a local public records request or the federal Freedom of Information Act (FOIA), may be considered private, personally identifiable information (PII) or privileged. These designations can apply in an ongoing investigation when personal information about an individual is disclosed.

Dark Reading
JUNE 8, 2022
Concentric AI's Karthik Krishnan joins Dark Reading's Terry Sweeney at Dark Reading News Desk during RSA Conference to discuss how artificial intelligence has transformed the security landscape.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Threatpost
JUNE 8, 2022
Rob Gurzeev, CEO and Co-Founder of CyCognito, explores external attack surface soft spots tied to an ever-expanding number of digital assets companies too often struggle to keep track of and manage effectively.

Dark Reading
JUNE 8, 2022
DeepSurface's Tim Morgan joins Dark Reading's Terry Sweeney at Dark Reading News Desk during RSA Conference to discuss how to fortify vulnerability management.

IBM Big Data Hub
JUNE 8, 2022
Implementing the right data strategy spurs innovation and outstanding business outcomes by recognizing data as a critical asset that provides insights for better and more informed decision-making. By taking advantage of data, enterprises can shape business decisions, minimize risk for stakeholders, and gain competitive advantage. However, a foundational step in evolving into a data-driven organization requires trusted, readily available, and easily accessible data for users within the organizati
Let's personalize your content