DinodasRAT Backdoor Targeting Linux Machines Worldwide
Data Breach Today
APRIL 1, 2024
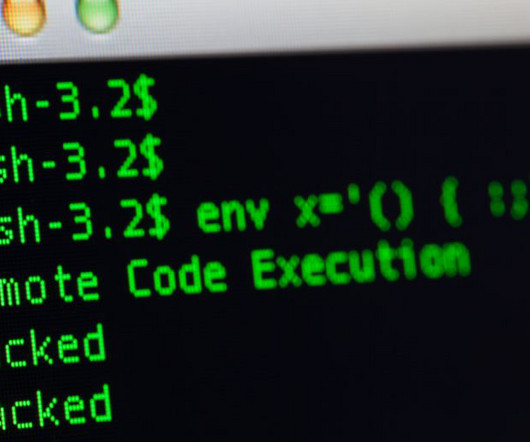
Chinese Hackers Have Used DinodasRAT Hackers are using a new version of a backdoor to target Linux servers and gain and maintain access in what appears to be an espionage campaign, warn researchers from Kaspersky. The hallmark of DinodasRAT's strategy is its sophisticated victim identification and persistence mechanisms.




































Let's personalize your content