Flaws in Lenovo laptops allow escalating to admin privileges
Security Affairs
DECEMBER 16, 2021
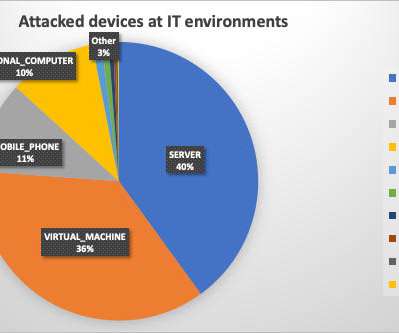
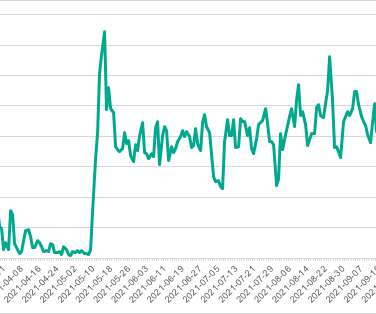
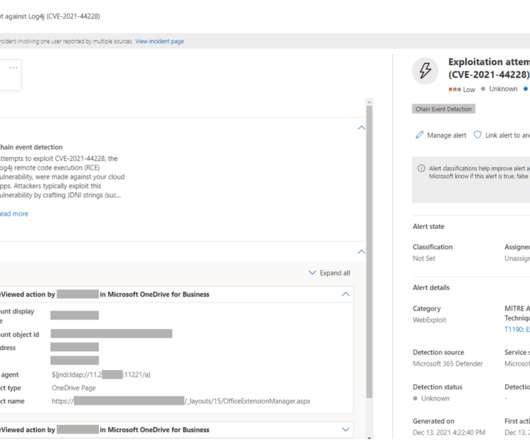
The ImControllerService service of Lenovo laptops is affected by a privilege elevation bug that can allow to execute commands with admin privileges. Lenovo laptops, including ThinkPad and Yoga families, are affected by a privilege elevation issues that resides in the ImControllerService service allowing attackers to execute commands with admin privileges.








































Let's personalize your content